A PRIVATE
COST-EFFECTIVE
ALTERNATIVE TO VIRUSTOTAL
Continuous AI-driven threat intelligence that's yours, not everyone else's.
YOU’RE IN GOOD COMPANY

INSTANT ANSWERS TO YOUR TOUGHEST SECURITY QUESTIONS.
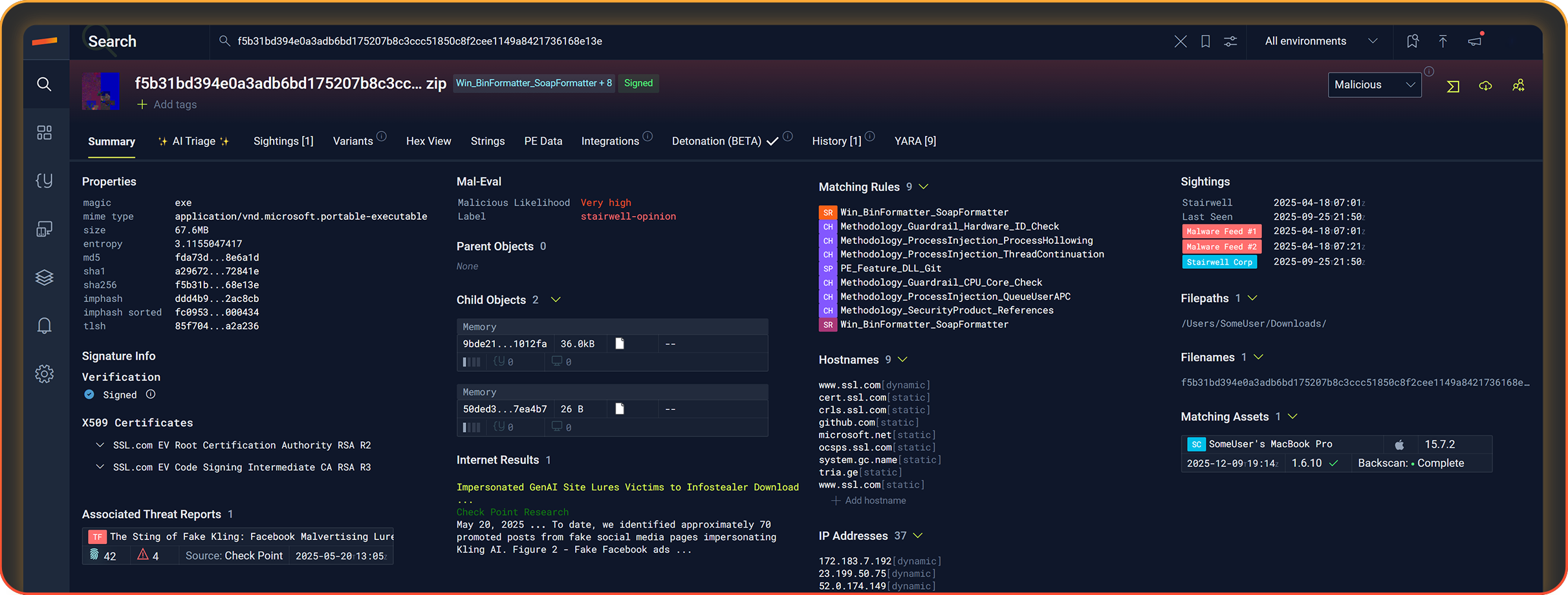
Is this file bad?
ANSWER SECURITY QUESTIONS.
IN ONE PLACE.
Each member of your team answers different questions using Stairwell.
- Is this file bad?
- How do I triage an alert?
- Do we have that hash anywhere?
- I need a second opinion on this EDR alert?
- Any IP addresses in that file?
- Any hostnames associated with that file?
- Is that file signed?
- How many machines have seen that file?
- Is this file bad?
- What are the historic resolutions of that domain?
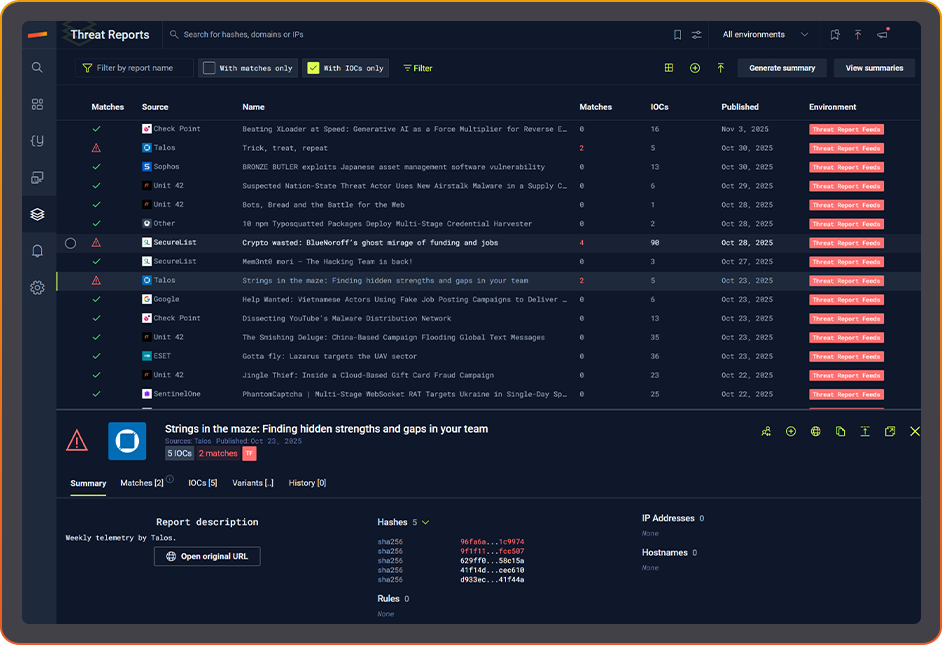
- Any IOCs from these threat reports in my enterprise?
- Any YARA rules triggered by that file?
- Do any files in my enterprise trigger any YARA rules?
- Are there variants of that malware anywhere?
- What other files are part of that malware campaign?
- Which other devices saw those files?
- What other files were on that machine on that date?
- Which devices contain Log4J?
- Which devices have unauthorized software?
THE PRIVACY TRADE-OFF
Your data becomes part of someone else’s corpus, and you rent back access through rising subscription fees.
Crowdsourced
Public
Your data powers others’ defenses and exposes your own patterns outside your enterprise.
Private
Secure
With Stairwell, our telemetry is yours and stays hidden in your own private vault.
STAIRWELL FLIPS THAT OLD CROWDSOURCED MODEL | PRIVATE, CONTINUOUS AND SOVEREIGN
PRIVATE THREAT INTELLIGENCE
Stairwell makes threat intelligence sovereign
It turns your environment into a private, continuously scanning intelligence system enriched by the world’s threat data but powered by your own. Every file ever seen, preserved and reanalyzed as new intelligence emerges. Every variant mapped, every intent explained, and every alert run to ground.
PRIVATE. CONTINUOUS. YOURS
Cybersecurity Expert, Hospitality
WHY IT WORKS
Built on a global-scale corpus of binaries, scripts, DNS and YARA matches.
Backed by structured AI reasoning, not opaque scoring.
Designs for continuous, indefinite analysis, not retro hunts.
Invisible to adversaries, integrates with your existing EDR.
Priced for daily operational use, not research-only budgets.
KEY FEATURES
Core capabilities of Stairwell’s malware and threat intelligence platform.
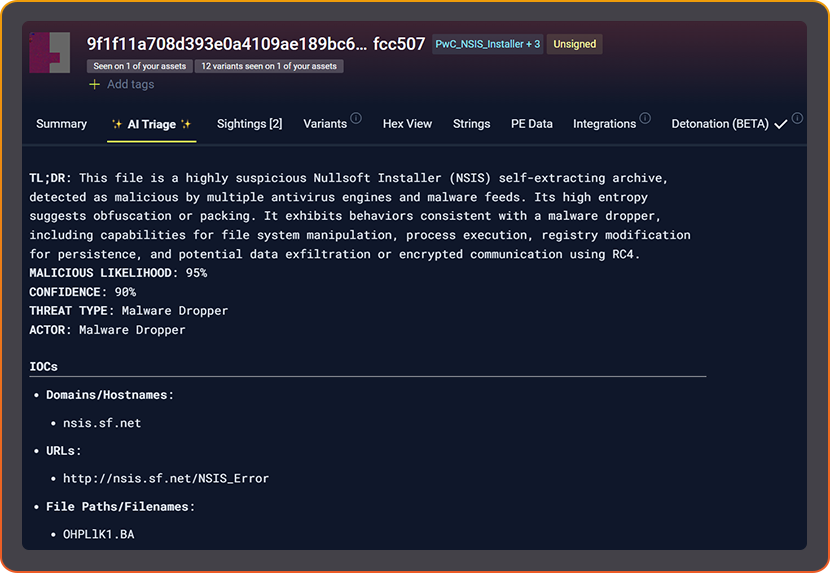
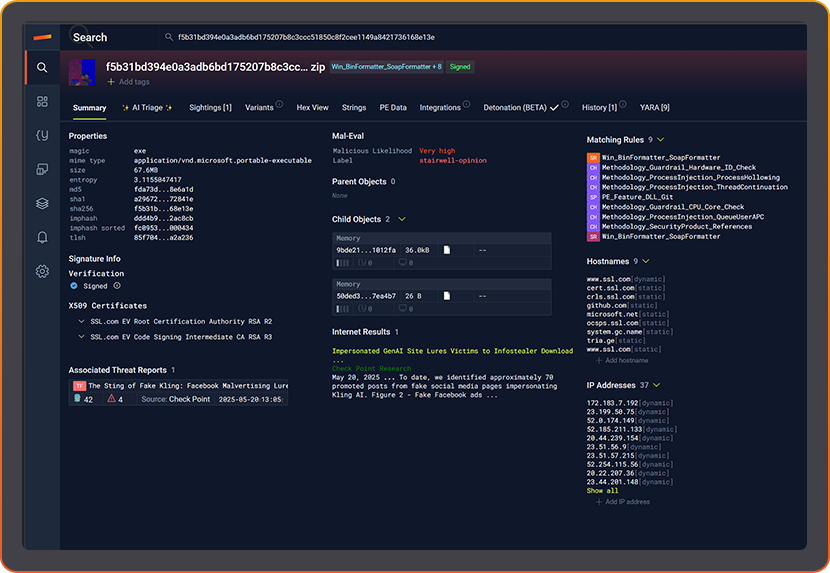
AI TRIAGE & MALWARE ANALYSIS
AI Triage steps outside the sandbox.
KEY BENEFITS
- Explains behavior, context, and intent instantly.
- Accelerates analyst triage and adjudication.
- Turns malware analysis into explainable intelligence.
MALWARE VARIANT DISCOVERY
Find what looks like other malware.
KEY BENEFITS
- Identifies polymorphic malware and re-used tooling.
- Builds family trees of related malware samples.
- Enables proactive variant-aware detection
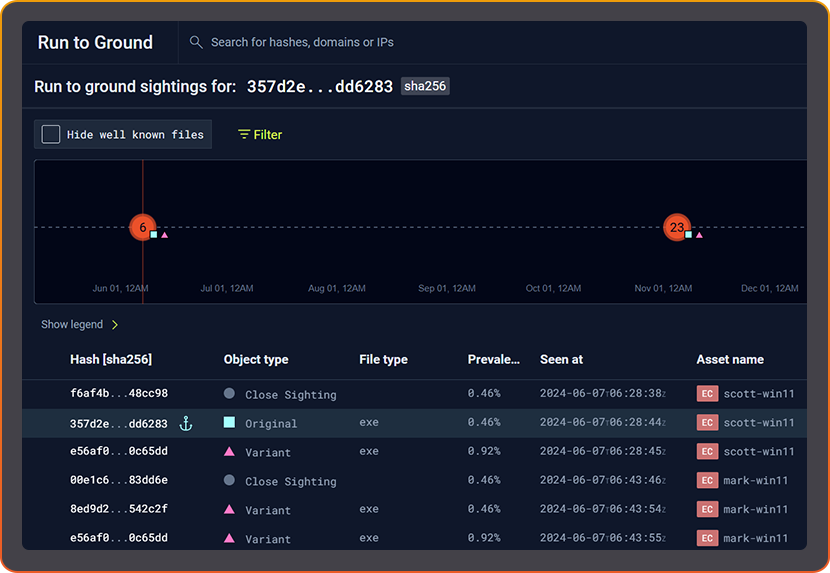
INSTANT INVESTIGATION WITH RUN TO GROUND
One click. Every variant. Every Trace.
KEY BENEFITS
- Enrich any EDR detection with full variant context.
- Connect related activity across time and hosts.
- Delivers forensics-level investigation capability to Tier-1 SOCs.
PRIVATE VAULT FOR YOUR DATA
Your data. Your Hindsight.
Preserve every executable. Continuously scan your own environment with the latest threat intelligence. Global visibility that never leaves your control.
KEY BENEFITS
- Permanent inventory of enterprise executables.
- Continuous retroactive detection as intel evolves.
- Encrypted, isolated storage for compliant visibility.
MALWARE THREAT INTELLIGENCE.
RE-IMAGINED.
OLD WAY
- Crowdsourced
- Point-in-time retro hunts
- Public uploads
- Verdicts and labels
- Rising costs (2–10×)
STAIRWELL
- Private vault
- Continuous reanalysis
- Private, encrypted environment
- Intent and lineage
- Owned visibility
- Fractional cost, daily use
SIMPLE PATH TO ENTERPRISE VISIBILITY
Three steps to grow into total malware visibility across your enterprise.
INVESTIGATE
Stairwell as your private VirusTotal
AUTOMATE
Hyper-scale investigations integrated into your workflow
DEPLOY
Unlock Stairwell with continuous analysis across your enterprise
PROTECT YOUR ENTERPRISE WITH AI & STAIRWELL THREAT INTELLIGENCE
Watch how Stairwell makes your SOC, Threat Intel, and Incident Response teams faster.
Stairwell: Private by design.
Continuous by default.
Stairwell: Private by design. Continuous by default.
The next evolution of threat intelligence is here.