ToolShell: Revealing Webshell Malware Variants and a New YARA Rule
What is ToolShell? A Microsoft SharePoint Vulnerability Explained
On July 18, 2025, Eye Security reported the mass exploitation of Microsoft’s on-premise SharePoint platform. SharePoint is a web-based collaboration tool widely used for document management, storage, and workflow automation within organizations. The vulnerability within SharePoint led to an exploit chain dubbed ToolShell.
The ToolShell attack chain leverages several critical vulnerabilities: CVE-2025-53770, CVE-2025-53771, CVE-2025-49704, and CVE-2025-49706. According to available intel, these vulnerabilities have been exploited by LuckyMouse APT, Linen Typhoon (APT27), Violet Typhoon (APT31), Storm-2603, and other China-aligned threat actors. The impact involves unauthenticated remote code execution (RCE) through deserialization flaws, bypass of MFA and SSO authentication mechanisms, theft of ASP.NET machine keys, deployments of ASPX webshells, and ransomware delivery.
What is Stairwell’s Workflow?
Step 1: Finding Variants using Variant Discovery
Leveraging Stairwell’s internal corpus of over 1.2 billion malware samples, we conducted a targeted scan for high-confidence variants of a known indicator of compromise (IOC) associated with the ToolShell attack chain. The goal is to identify modified, often undocumented, versions of the original malware that may evade standard detection.
Original ToolShell sample (SHA256): 92bb4ddb98eeaf11fc15bb32e71d0a63256a0ed826a03ba293ce3a8bf057a514
Through Variant Discovery process, we uncovered two previously undocumented variants of the ToolShell ASPX webshell:
- SHA256: 27c45b8ed7b8a7e5fff473b50c24028bd028a9fe8e25e5cea2bf5e676e531014
- SHA256: 10e01ce96889c7b4366cfa1e7d99759e4e2b6e5dfe378087d9e836b7278abfb6
These discoveries highlight the utility of large-scale corpus analysis for surfacing stealthy, evolved threat artifacts.
Step 2: Examining Hilbert Curves Visualization
To assess similarity across these samples, we used our Hilbert Curves implementation which enables two capabilities:
First, the quick visual assessment of file composition (see the image below)– shows mostly ASCII values (blue tones) with null bytes (green tones).
Hilbert Curve of original ToolShell malware sample (SHA256): 92bb4ddb98eeaf11fc15bb32e71d0a63256a0ed826a03ba293ce3a8bf057a514
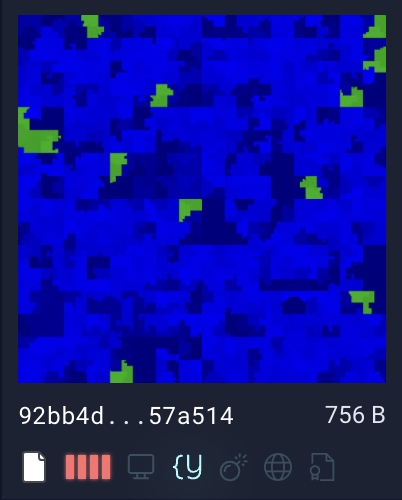
Second, we have direct visual comparison between the original malware sample and the two newly discovered variants. By examining the Hilbert Curves of the original sample (above) alongside those of the variants (below), we observed a shared composition – large regions of blue tones, indicating dense ASCII content, interspersed with segments of green representing null bytes. This visual similarity suggests that the variants retain a comparable structure and content to the original. To further validate this observation, we developed a tailored YARA rule designed to detect these patterns across similar samples.
Hilbert Curves of two newly discovered ASPX webshell variants:
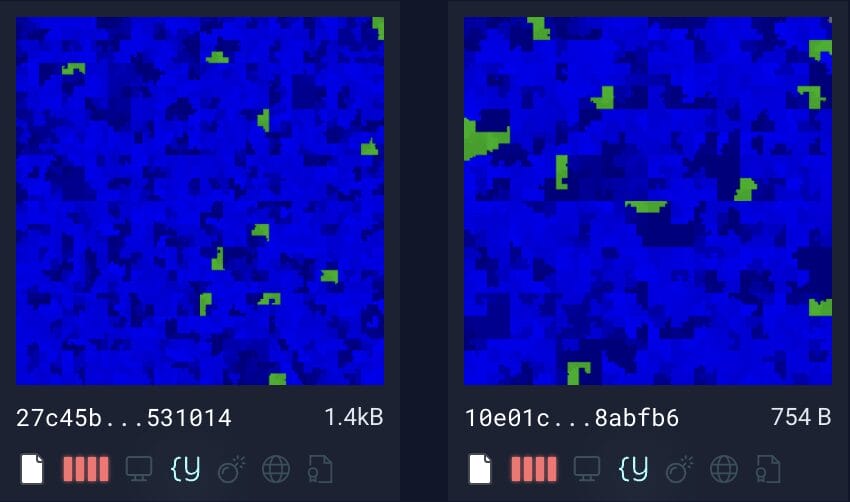
SHA256 hashes of the ASPX webshell variants identified by Stairwell.
- 27c45b8ed7b8a7e5fff473b50c24028bd028a9fe8e25e5cea2bf5e676e531014
- 10e01ce96889c7b4366cfa1e7d99759e4e2b6e5dfe378087d9e836b7278abfb6
Step 3: New ToolShell YARA Rule for Detection
Using the above findings, we authored a YARA rule to identify this family of ASPX webshells in your environment:
rule ToolShell_SharePointCVE_ASPX_Webshell {
meta:
author = "Evelyne Diaz Araque ([email protected]"
description = "Detects ASPX Webshell used in the ToolShell SharePoint vulnerability."
date = "2025-08-01"
sha256 = "92bb4ddb98eeaf11fc15bb32e71d0a63256a0ed826a03ba293ce3a8bf057a514"
strings:
$s0 = " var mkt = sy.GetType(\"System.Web.Configuration.MachineKeySection\");" ascii
$s1 = "var sy = System.Reflection.Assembly.Load(\"System.Web, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a\");" ascii
$s2 = "<script runat=\"server\" language=\"c#\" CODEPAGE=\"65001\">" ascii
condition:
(2 of ($s0,$s1,$s2)) or
(1 of ($s1,$s2,$s0)) or
(1 of ($s2,$s0))
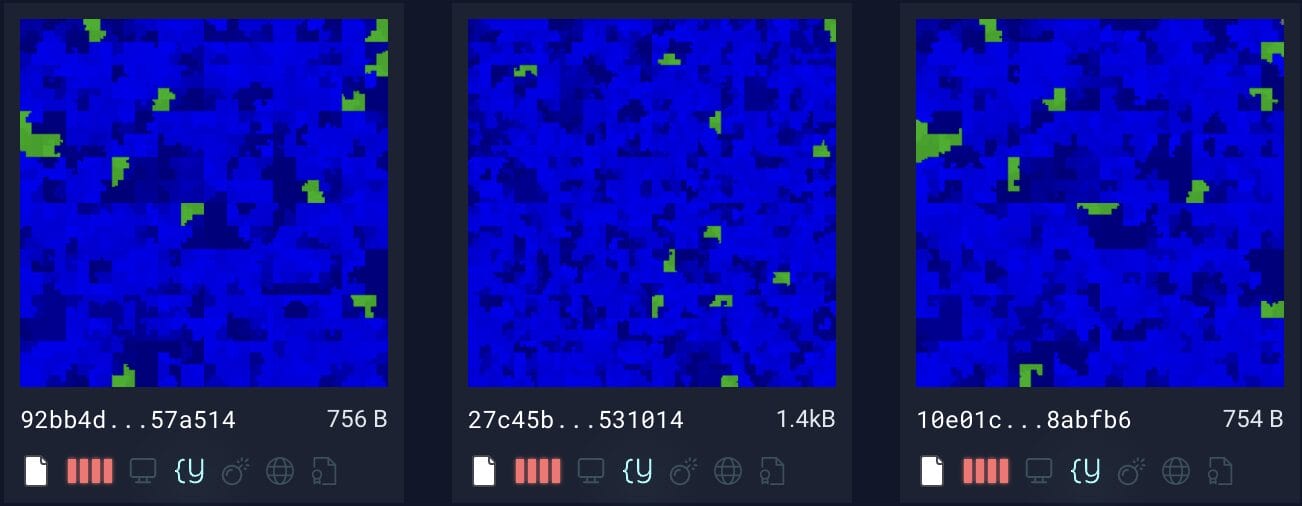
}This rule successfully matches both the original webshell sample and the newly discovered variants, enabling broader detection coverage. Using Hilbert Curve visualizations, we observe that all three files share a similar composition – predominantly ASCII-readable content (blue tones) and null bytes (green tones). Notably, the samples with SHA256 hashes 92bb4d… and 10e01c… display near-identical structural patterns and size, reinforcing the rule’s precision in detecting closely related variants. Furthermore, the rule also detects 27c45b…, a sample that deviates from the original’s structure yet remains malicious, demonstrating the rule’s robustness in identifying both tightly and loosely coupled variants.
Help your team stay ahead
The ToolShell exploitation of Microsoft’s SharePoint highlights the continued targeting of enterprise infrastructure by well-resourced threat actors.
After a combination of proactive malware variant discovery, behavioral visualization using Hilbert curves, and tailored YARA detection, Stairwell enables defenders to stay ahead of adversaries. Organizations should apply available patches, monitor for known indicators, and incorporate detection rules like the one provided above to strengthen their response posture.



