Are your SVGs Malicious? Hiding malware in your graphics files
SVGs are an overlooked attack vector
Though often overlooked in favor of more traditional document formats like PDF or Office files, SVG files are an increasingly common choice for threat actors. Built on XML and designed for the web, SVGs can embed JavaScript, link externally, and still render successfully in browsers…even when malicious. When misused, these are capable of delivering payloads, evading detection, and acting as the very beginning of more complex attacks.
We’ve been seeing more SVG-based attacks recently, and many people are sleeping on this vector. We’ll go over the common patterns of exploitation, how YARA rules can be written to help detect suspicious versions of these files, as well as how Stairwell’s AI Triage can instantly surface threats deeper within for your teams — even with these deceiving file types.
What is an SVG file?
An SVG (Scalable Vector Graphics) file is an XML-based image format used to define digital images for the web. They are browser-native and commonly used for logos, UI icons, and dynamic charts. Unlike JPEG or PNG, SVGs are plaintext and human readable, and built on a structured tag-based structure similar to HTML. Because they support features such as styling, animations, and JavaScript, SVGs are essentially hybrid documents that fall somewhere between image and application, and are not inherently malicious.
How threat actors abuse SVGs
The thing about SVG files is: they appear innocuous. Thus, these are often trusted and overlooked, particularly when used as email attachments or web-hosted resources. But because they support <script> blocks, inline JavaScript, and references to external content, attackers can abuse them to:
- Redirect users to phishing pages, malicious domains
- Load JavaScript payloads (eval, atob, document.write)
- Act as lightweight HTML smuggling components
- Host credential stealers directly in the image
A recent, real-world example is Shadow Vector. The attackers behind this phishing campaign targeting users in Colombia use a newly recognized subtechnique, listed in the MITRE ATT&CK framework, called SVG smuggling. These graphics are used to embed harmful content and are deployed via spear-phishing emails. When opened in a browser, the SVG redirects to public file hosts like Dropbox or Discord, downloading a mix of legit binaries and malicious DLLs. These ultimately launch remote access trojans (RATs) through a chained injection sequence.
It’s becoming more frequent that attackers are utilizing SVG files. Back in May of 2025, Sublime Security mentioned seeing a 47,000% rise in SVG payloads within phishing emails. Many SVG attacks fall under PhaaS (Phishing-as-a-Service), commodity malware, or malspam, but more advanced threat actors such as SocGhoulish have been noted to take advantage of these.
YARA to detect suspicious SVG files
While direct SVG file downloads are relatively uncommon in typical user workflows, that doesn’t make them undetectable. SVG-based attacks tend to follow a predictable, multistage sequence: JavaScript runs, a second-stage payload is fetched, persistence is established, and eventually, reconnaissance or lateral movement begins.
Catching the initial file, or a copy of it later during incident response or retrohunting, can expose early-stage indicators and help trace the full kill chain. In cases where SVG files do touch disk, YARA becomes an effective hunting mechanism. YARA rules are particularly useful in email gateways, web proxies, and sandbox platforms. These act as chokepoints for SVG inspection before they reach the endpoint.
Retrospective analysis of files, like what Stairwell provides, becomes essential for piecing together what happened. Malicious SVGs still manage to evade controls due to:
- Low inspection priority in many pipelines
- The use of obfuscated JavaScript to evade static detection
- Hosting on legitimate domains that sidestep traditional URL filtering
Stairwell’s YARA Rule to Detect SVG files
This is where we can play a critical role. Our platform allows incident response (IR) teams to use YARA to search across every file ever seen in their environment, current and historical. Even if a suspicious SVG was first seen six months ago, we can flag it today. This gives you retrospective visibility into where suspicious SVG files have landed (even after a breach), prevalence context, pivoting capabilities across embedded indicators of compromise, and a deep assessment to scope incidents faster.
We’ve created a hunting rule to identify SVG files containing embedded scripting content that could indicate malicious activity. This rule detects SVG files with JavaScript elements and obfuscation techniques commonly used in weaponized graphics files, providing broad detection coverage best for threat hunting workflows:
rule SVG_Suspicious_Script_Content {
meta:
author = "[email protected]"
description = "Hunt for SVG files with script tags, javascript: URIs, or obfuscation functions (eval, atob, fromCharCode, CDATA)"
strings:
$svg_start = "<svg" nocase
$javascript = "javascript:" nocase
$script_tag = "<script" nocase
$eval = "eval(" nocase
$atob = "atob(" nocase
$fromcharcode = "fromCharCode(" nocase
$cdata = "<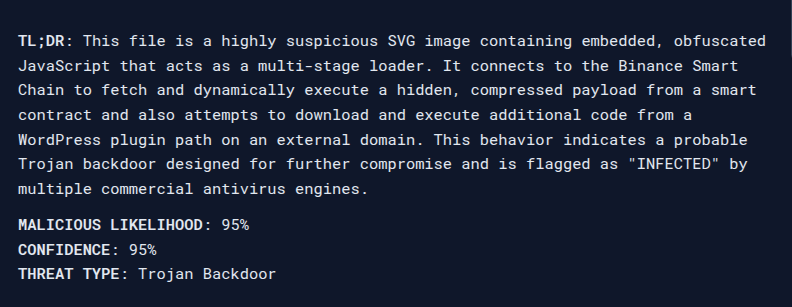
No headache, no waiting around — just analyzed in seconds, while providing a full breakdown of a file’s behavior and its red flags.
Final Thoughts
SVGs are usually shrugged off as “just images”, but their scripting capabilities make them a truly viable malware delivery vector, and that’s what makes them so attractive to attackers. They appear benign, bypass naive filters, and support multiple layers of obfuscation. They succeed at this because they don’t look like malware. No macros, no EXEs, no scary PE headers, but an image.
With our YARA and AI Triage capabilities, we’re able to bring some insight into these unsuspecting files and hunt for common scripting patterns, encoded payloads, and redirection logic. We can identify threats and provide answers instantly, and these files are no exception. As threat actors continue to expand their use of web-native formats, defenders should be treating SVGs as part of the broader attack surface.



