Prometei Evolves: Stairwell identifies new variants and publishes 3 new YARA rules
Malware and botnet Prometei continues to evolve. The Stairwell Threat Research team uncovers 53 variants of Prometei and shares three new YARA rules to support detection efforts.
How Prometei Re-appeared
On June 20th, researchers at Palo Alto Networks released a report on the modular cryptocurrency botnet and malware, both by the name Prometei.
Prometei was first discovered in July 2020, but evidence suggests it has actively been in development since 2016. The malware family recently made a comeback with evolved capabilities, with intel reporting a surge of activity since March 2025. The botnet targets both Linux and Windows operating systems and has utilized EternalBlue, SMB, and RDP exploits, which are security vulnerabilities that allow the spread of malware between computers on the same network.
Prometei’s main objectives are credential theft and cryptocurrency mining, specifically Monero. This malware is difficult to detect because it uses a domain generation algorithm (or DGA, a method that malicious software uses to automatically create numerous different website addresses), and it self-updates. What makes it dangerous is its architecture; Prometei contains different components that work together to break into systems, steal data, and communicate via command-and-control servers. Consistent with the original Palo Alto report, we will be focusing on Linux samples and variants.
Variant Visibility with Stairwell
Malware variants are modified versions of known malicious software, recompiled or altered to evade detection, target different systems, or continue operations. These variants often share much of the core functionality of the original malware, but differ in enough technical or structural traits to just fly under the radar of signature-based tools. Identifying malicious variants is crucial to analysis, as they often suggest the continuation or evolution of an active threat campaign.
Stairwell gives threat researchers capabilities that go beyond what standard EDR tools allow, delivering deeper intelligence into malware samples and analyzing variants in ways not possible otherwise – an example is the visibility we deliver through our Variant Discovery capability. Variant Discovery gives increased visibility by automatically clustering related malware based on shared behavior and structure. Unlike static signatures or hash-based detection, this approach uncovers relationships even when code has been heavily obfuscated or repackaged. It allows analysts to trace threats across campaigns, and enables quick pivots.
Using the IOCs provided in Palo Alto’s report, Stairwell identified 53 additional Prometei variants using Variant Discovery within our platform. All 53 of these are unreported Prometei variants that share strong technical overlaps and infrastructure, giving us high confidence in attribution.
For example, using this capability and pivoting off the hash 205c2a562bb393a13265c8300f5f7e46d3a1aabe057cb0b53d8df92958500867 from Palo Alto’s report alone leads us to 23 variants (or 23 Prometei samples) shown below in the screenshot. Here, we see the original Prometei file listed first and below are four of the variant samples that are 99% matches. Interestingly each variant includes the Hilbert curve images on the left which visually show similarity between the malware variants:
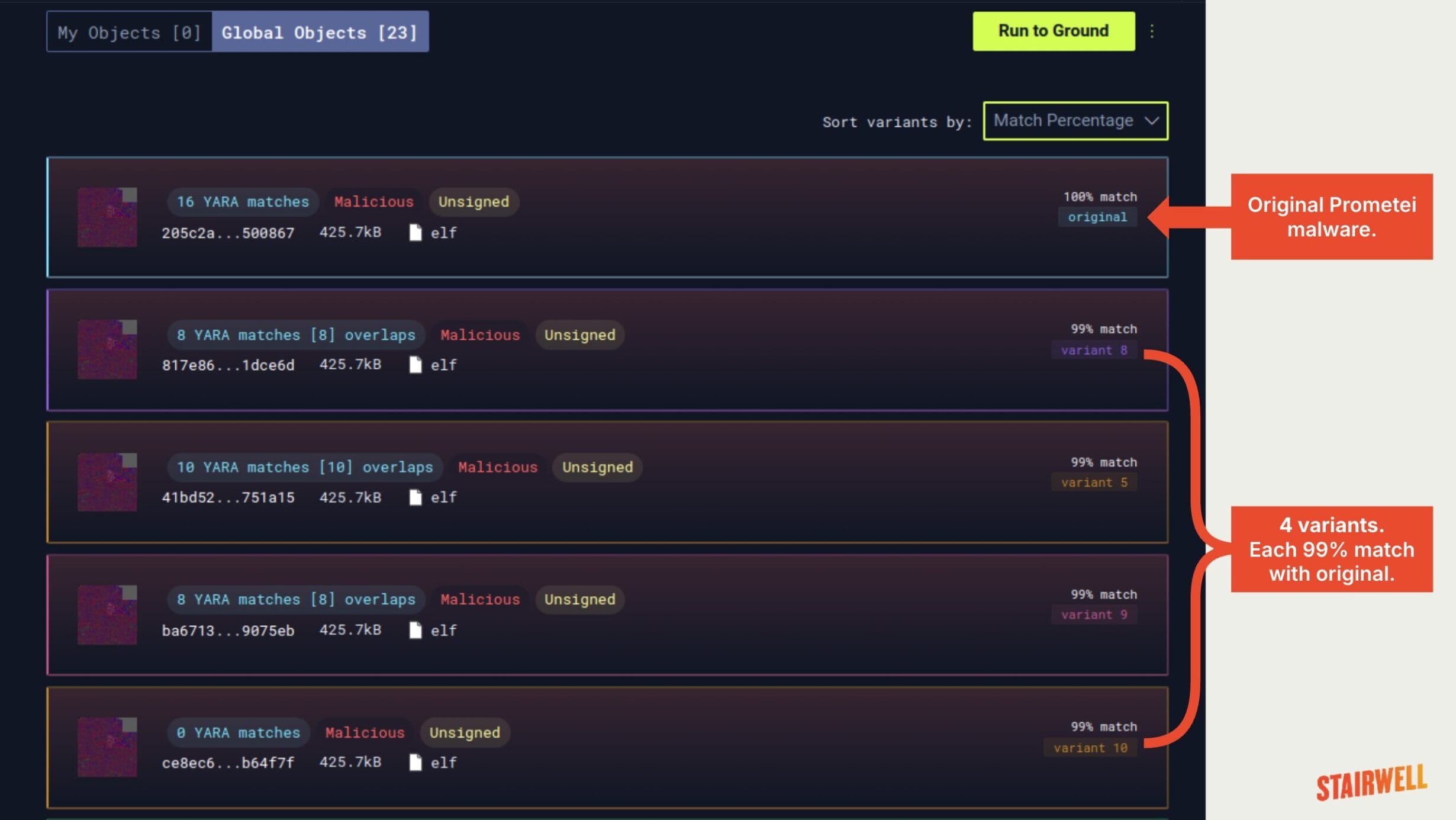
Variant Discovery gives defenders an advantage by exposing the different techniques of malware authors and seeing through their attempts at evasion. These capabilities demonstrate the strength behind the Stairwell platform and its clustering power, as well as its analytical depth and unique ability to surface lesser known variants of established malware families.
Three YARA rules to detect Prometei
YARA remains one of the most powerful tools in a threat hunters kit for surfacing threats at scale, as it’s capable of identifying malware based on patterns in binary, strings, structure, and even behavioral artifacts. At Stairwell, our infrastructure continuously scans every file we ingest with an extensive suite of YARA rules, developed both in-house and sourced from the broader threat research community to ensure we catch both known and unknown threats.
Building on Variant Discovery, and in alignment with Palo Alto’s research, we developed a high-fidelity YARA rule to go beyond this recent campaign and to detect both Prometei ELFs and PE files:
rule Prometei_UPXJSON_config
{
meta:
description = "Detects Prometei malware with UPX and JSON config"
author = "[email protected]"
date = "2025-07-01"
strings:
$upx_magic = { 55 50 58 21 }
$overlay_offset = { F4 00 00 00 }
$json_config = "{\"config\":" ascii
condition:
all of them and
filesize >=404787 and filesize <= 436122
}To detect newer and Linux-based Prometei samples specifically first seen since since their comeback in March 2025 (even in their UPX-packed form), we’ve also created a strings-based rule:
rule Prometei_ELF_Strings
{
meta:
author = "[email protected]"
date = "2025-07-01"
description = "Detects recent Linux variant of Prometei as of July 2025; developing botnet and malware"
strings:
$s1 = "HTTP/1.04Ho&:$" ascii
$s2 = "9999 !\"#9999$%&'9999()*+9999,-./9999012399994567999989:;9999<=>?9999@ABC9999DEFG9999HIJK9999LMNO9999QRST9999UVWX9999YZ[\\9999^_jk9999rstu9999" ascii
$s3 = "{\"config\":1,\"id\":\"4H92JnV9tt6z96Rf\",\"enckey\":\"Vxph1YmKABXOJJXWet8BOStgbCVJ9w11E807q4AA8hrb7YTKrOWeF13pEL9KGJb6QO82jV07QndS98Ygi9YJ7FJ5L/LXDpZ5EQJZhBXafw011kOMjfmhyA2p00Mk5d11bZkF1SfkNwY1uoQdJ+nlDDhGQVyTa2bndS0XmDq5wWs=\"}" ascii
$s4 = "bf8###g89 WVQ" ascii
$s5 = "Nng ups_9ILP32_OFF" ascii
$s6 = "bOtEuMN2Bpx2" ascii
condition:
5 of them
}Lastly, we created a command-and-control focused rule based on recent network activity since March 2025:
rule Prometei_C2_2025 {
meta:
author = "[email protected]"
desc = "Hunt for recent Prometei C2 as of June 2025"
strings:
$ip = "152.36.128.18" ascii nocase
condition:
$ip
}With security researchers noting a significant surge in Prometei samples and activity, organizations need to prioritize detection capabilities to defend against this evolving threat, especially given Prometei continues to incorporate new methods into its already dangerous toolkit to slip under the radar in some public reporting. By combining retroactive Variant Discovery and static detection, we’re surfacing both the known and next wave of threats.
Stairwell Customers Have Visibility
Stairwell customers easily see if any of the variants or hashes are within their environment by looking in the Threat Reports section.
Better still, customers know its files within Stairwell were scanned and are absent of any of the Prometei malware or variants if they see the Stairwell green check mark which lets their security team know there is nothing more for them to do. Stairwell has done the research in their environment for them and their Prometei Health check is all clear.
Five Prometei variant hashes
817e8682000f34a40d91a113af4aa755e5c424a31f1153b373062ce34b1dce6d
c2fddbc523eee985178253026259f44016e9646536b37e98602315256845963a
ce8ec66ca2c677feb87037de53a37433b9422f0ab57ba5bdf68c521db9b64f7f
d8551d6f415da2482b0827d2e7c0f7bbea2437757344b9f31c3bd69b895e29fe
69f4870aa9cd29313098c744155830074b81b03f19ed101c32299fa08d54f9c5
These five hashes represent just a glimpse of the 53 distinct variants our team uncovered using Stairwell’s platform. This is the depth of analysis available when you’re not limited by traditional tooling. If you’re interested in the full dataset, or curious how we can help your team surface threats hiding in plain sight, our sales team would love to connect.



