Security alert enrichment: ShadowPad variants
While reviewing Symantec’s recent Redfly report detailing new ShadowPad activity targeting critical national infrastructure (CNI) organizations, the Stairwell Threat Research Team zeroed in on a couple of interesting variants of the ShadowPad sample provided in the report (SHA256: 656582bf82205ac3e10b46cbbcf8abb56dd67092459093f35ce8daa64f379a2c). ShadowPad is a modular malware family first seen in 2015 that has been used by multiple APT actors originating from the People’s Republic of China (PRC). According to their report, Symantec has decided to cluster these intrusions as Redfly due to their exclusive focus on intrusions in CNI targets.
As stated by Symantec, “…the frequency at which CNI organizations are being attacked appears to have increased over the past year and is now a source of concern. Threat actors maintaining a long-term, persistent presence on a national grid presents a clear risk of attacks designed to disrupt power supplies and other vital services in nation-states during times of increased political tension.”
The ability of Stairwell to go beyond the limitations of tools like EDR (like providing coverage on your security, network, and OT appliances) – paired with its ability to allow users to view a threat report like Symantec’s within the Stairwell platform and swiftly pivot from the reported IOCs to uncover additional samples through Stairwell’s Variant Discovery – accelerates the operations of cybersecurity teams to better protect organizations and critical national infrastructure.
Below are additional variants of the ShadowPad sample that organizations should look for within their environments, as well as queries Stairwell customers can use to quickly search for reported traces of activity.
Alert enrichment
The first sample variant (SHA256: f515d2eb614b9744d0bfa8852965a9272948e3639d8f306492af4c942cd6ad3d) showed a 64% similarity to the one provided in the Symantec report and utilized the C2 domain operatingbox[.]com. This domain had been previously associated with intrusions into ICS systems in Pakistan, as reported by Kaspersky.
The second sample variant (SHA256: 48ac2ca316e636109524e72c771afc7e4592f0a6c1de827985aa090f17b98879), with a 79% similarity, employed the C2 domain rtxwen[.]com. This domain has not been documented in other known reports.
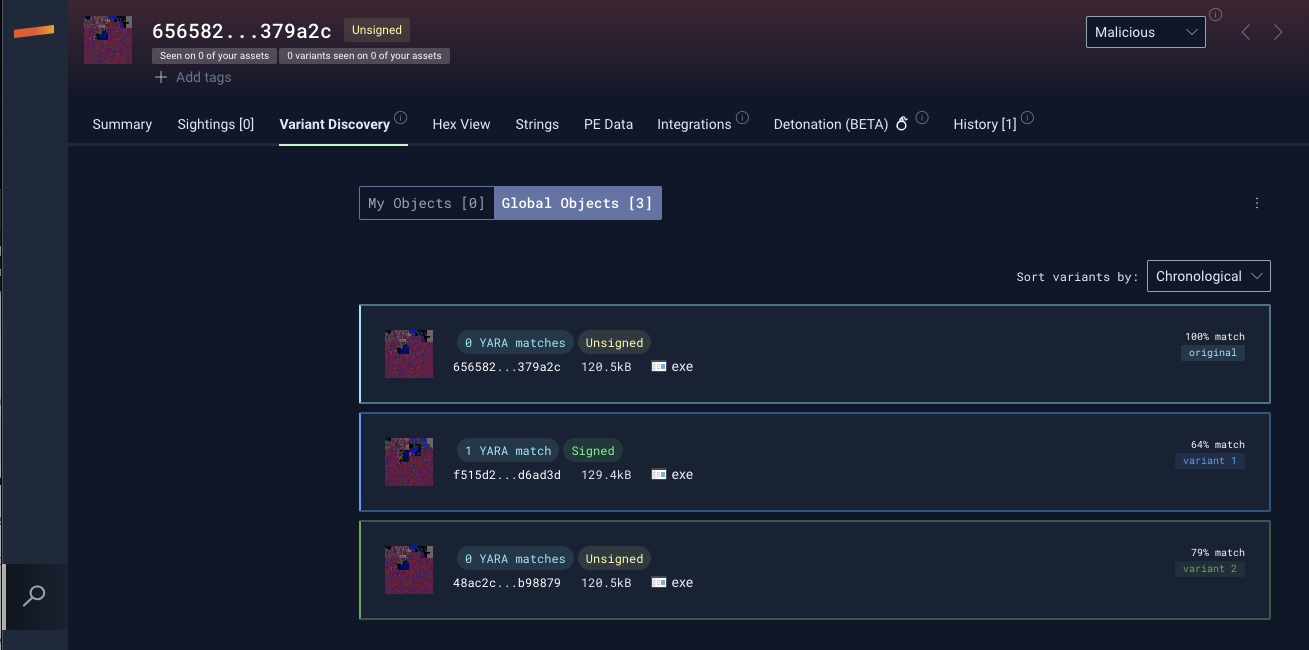
Pivoting on the Imphash (f7e300e1499fb7427b3ad9dca6fd3d47) of these 3 samples, we identified 4 additional ShadowPad variant samples:
231d21ceefd5c70aa952e8a21523dfe6b5aae9ae6e2b71a0cdbe4e5430b4f5b3
abee0b7805ff7092c14f02718742b52502d333c931316aeabd7866fd5bfd916f
c276387325c8baa259e89eb3acf96c12c426cdb3d70a3551d565c14f21391c4f
a8eddbc68d7af544d9d8671ccac13c6ab5686fe6cd26ffc72420636a813ca4deIt’s important to note that, while these variants share similarities, we cannot conclusively determine that they are all being used by the same threat actors. ShadowPad is believed to be privately sold to a select number of actors.
Stairwell queries
In the report, Symantec also shared a timeline of observed activity. From those details, the Stairwell team is sharing some queries that can be used in the Stairwell platform to identify possible traces of activity.
Keylogger stores captured keystrokes in the following:
object.path.contains(r"\Intel\") && object.name == r"record.log"
Packerloader looks for the following:
object.name == r"tmp.bin"
Two observed filenames where ShadowPad was copied in VMware directories:
object.path.contains(r"C:\ProgramData\VMware\RawdskCompatibility\virtual\") && object.name == r"vmrawdsk.exe"
object.path.contains(r"C:\ProgramData\VMware\RawdskCompatibility\virtual\") && object.name == r"mscoree.dll"
About Stairwell
The Stairwell platform helps organizations automate the detection and response efforts related to the threat outlined in this report and equips them with the tools needed to proactively monitor for future attacks.
By collecting every executable file in an organization’s environment, the Stairwell platform enables security teams to stay a step ahead with AI-based detection and analysis of malware and unknown variants present within your environment.
Conduct a full threat assessment in minutes, automatically and continuously uncover malware and its variants, and instill confidence that you’re better protected now, in the past, and in the future. Visit the Stairwell platform page to learn more.



