Stairwell integration with Google Security Operations: Enrich IOC telemetry to operationalize threat intel faster
We are excited to announce the general availability of the Stairwell integration with Google Security Operations. Organizations can now get Stairwell’s enriched malware data delivered automatically into Google Security Operations to help teams detect threats and operationalize threat intelligence faster.
What is Stairwell
Stairwell solves the problem of detecting malware hiding in an enterprise by bringing a signal intelligence approach to gathering data that determines the connections from threat intelligence, malware libraries, and threat report IOCs to the actual files in your enterprise. Unlike log-centric solutions that are easily evaded, require costly and unsustainable storage, and take too long to search, Stairwell finds more malware by continuously analyzing your most important data set: your files.
With Stairwell you have a cost-effective platform that answers any question from your threat intelligence, SOC analysts, and incident response experts–in seconds. Stairwell is a search engine for malware and vulnerable, or non-compliant files within your enterprise.
Architecture
The enrichment call is simple: when a case appears in Google Security Operations, the IOC is automatically forwarded to Stairwell. From there, the IOC is matched against Stairwell’s malware corpus or a file in your organization’s private vault. The response is structured and enriched: verdicts, YARA Rule matches, prevalence data, related variants and technical indicators like registry keys, embedded files, or persistence mechanisms.
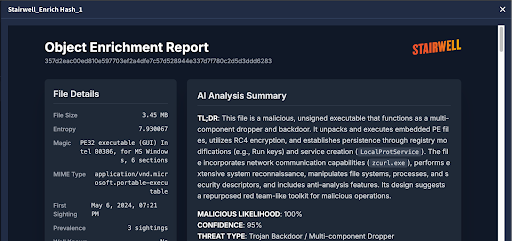
The enrichment goes beyond just “malicious/benign” designations to include AI-driven summaries, unpacked payloads, dropped file lists, registry entries, and key considerations like anti-analysis tricks or invalid signatures. Those details flow back into the Google Security Operations case timeline automatically.
Analysts don’t need to pivot into another platform or detonate files in a sandbox. When opening the case, the enrichment is already there, letting the analyst know what the file actually does and how it connects to others.
How to connect Stairwell to Google Security Operations
Getting Stairwell enrichment into Google Security Operations is straightforward. Install the Stairwell package from the Google Security Operations Marketplace > Response Integrations, then create a new instance under Response > Integrations Setup. Add your org ID, user ID, API key, and API root, save, and run the test to confirm connectivity.
After the integration is saved, you can enable enrichment views inside cases. In Google Security Operations settings, add the Insights widget to your default case view. This ensures enriched IOC details, hashes, hostnames, and IPs, appear directly in the case timeline where analysts work.
From that point forward, the integration is part of your playbook builder. When creating or editing playbooks, just search for Stairwell in the step selection panel. The actions are already prebuilt, complete with widgets for visualizing enrichment results.
This setup gives you a consistent pipeline: cases appear, IOCs are identified, Stairwell enriches them, and the results are presented inline to the analyst without extra pivots or context switching.
See more on our setup here – https://docs.stairwell.com/docs/google-secops-integration
SOAR Playbook Building Block
The enrichment block is trigger-agnostic. It doesn’t matter how the case was created – whether from an EDR alert, a SIEM correlation, or even another playbook spawning a secondary case. If the case contains a hash, IP, or hostname, the playbook can enrich it with data from Stairwell.
Use case 1: Event from Google Security Operations enrichment (automated via playbook)
Once the Stairwell enrichment action is in a playbook, it can run automatically. Any new case with an IOC can trigger enrichment without analyst involvement.
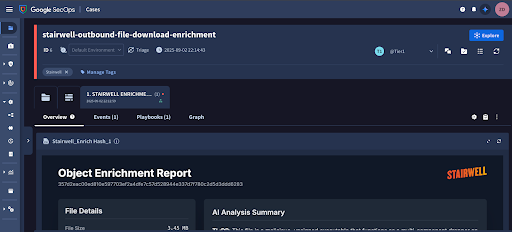
For example, a SIEM correlation rule generates a case containing a hash. The playbook runs, Stairwell enriches the IOC, and the verdict, behavior summary, and related variants are appended to the case timeline. If that case spawns another, the enrichment applies there as well.
The workflow is consistent: no matter the source of the IOC, it arrives in Google Security Operations already carrying Stairwell context. Analysts spend their time deciding what to do next, not chasing raw indicators.
Use case 2: Use variant discovery to help draw correlations between cases
Two cases land in the SOC queue: one tied to a shady driver, the other to a DLL being sideloaded through a LOLBin. At first glance, they look like completely separate issues. Different techniques, different alerts, something you’d normally triage and close without ever linking together.
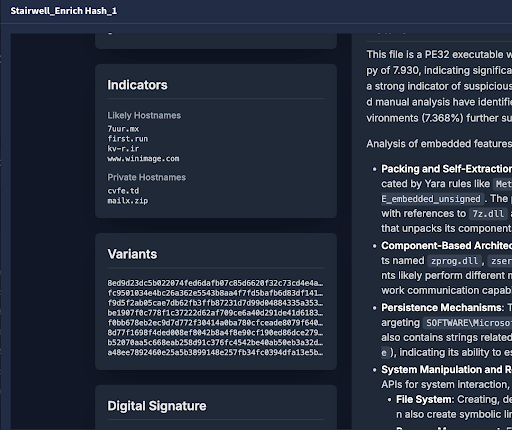
But when the playbook runs its Stairwell hash enrichment action, both file hashes get sent in for analysis. Through Stairwell’s Variant Discovery, the driver and DLL appear as variants of each other, tied together by similarities in the files. What looked like noise in two different places turns out to be connected pieces of the same campaign.
See below in the image how we enrich your existing alerts with “Variants” of the original file to tie your cases together.
Summary
That changes how the SOC responds. Instead of closing out two medium-severity cases, they treat it as one bigger incident: broaden containment, wipe out the whole family of artifacts, and brief leadership with a clear, unified story. It’s the difference between working alerts in isolation and actually understanding the campaign behind them.
The Stairwell integration with Google Security Operations enables enterprises to automatically enrich their IOC telemetry with Stairwell’s malware data and Variant Discovery. This provides analysts with deeper context, faster correlations, and the ability to connect cases into coherent campaigns without leaving their workflows.
With enrichment delivered inline, teams can operationalize threat intelligence with fewer pivots and greater confidence in their response. To learn more about how Stairwell can enhance your Google Security Operations environment, visit Stairwell.com



