Stepping into the unknown: Uncovering espionage malware with Stairwell Variant Discovery
Last week, ESET shared some research into espionage activity they observed targeting a government organization in Guyana. Based on the tooling used (PlugX) and the political timing identified by ESET, it is believed this activity is from a state-sponsored threat actor originating from the People’s Republic of China (PRC). On the Stairwell research team, we know firsthand that analysis and research are collaborative and iterative. When our friends share research, we regularly evaluate and start looking for other things that could be related to help further the story.
One area in which Stairwell can expand on and provide significant value is finding unknown variants. Variant analysis, as a whole, is a powerful tool for identifying copies of malware that may be difficult to identify using traditional pivoting methods. Stairwell’s Variant Discovery tool allows researchers to explore and analyze potential new malware variants. By leveraging Variant Discovery, researchers can quickly pinpoint similarities and differences among different malware samples, shedding light on evolving techniques employed by malicious actors.
Of the four hashes that ESET shared in the blog, two were already available in Stairwell to examine, along with the infrastructure IPs and domains.
When we look at these using Stairwell’s Variant Discovery, the first hash (SHA256 hash: d17fe5bc3042baf219e81cbbf991749dfcd8b6d73cf6506a8228e19910da3578) shows us three similar samples with one of them being another sample mentioned in the ESET report (SHA256: e0f109836a025d4531ea895cebecc9bdefb84a0cc747861986c4bc231e1d4213).
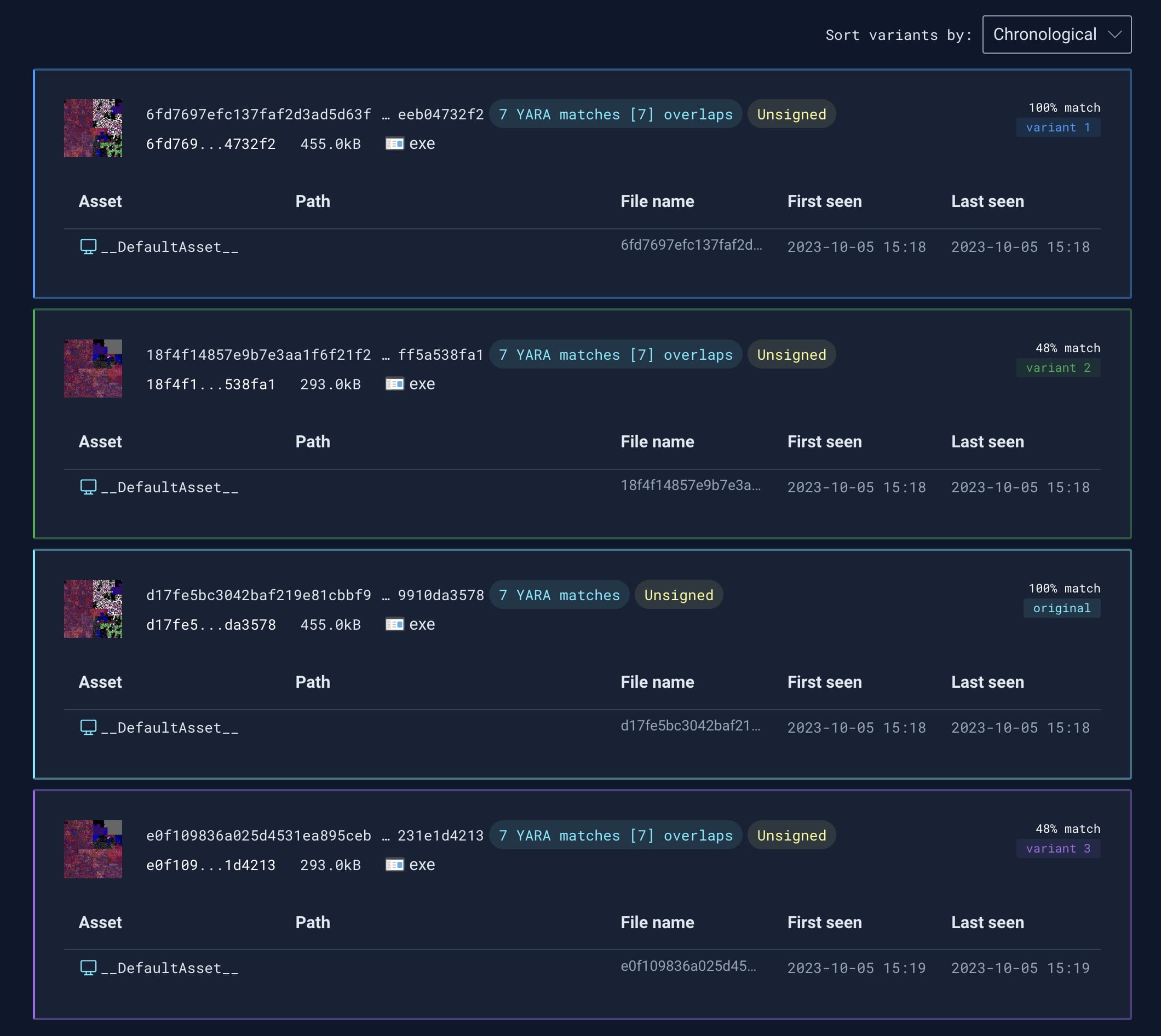
The details of the two variants discovered are below:
Running Variant Discovery on these two uncovers an additional unknown sample that was also not mentioned in the report:
From the samples uncovered with Variant Discovery so far, there are some common elements. The most notable are the build paths that are worth exploring. While the drive letter changes, the build path starting with ShenTou remains consistent, potentially indicating the developer is working off a shared network resource. When crafting a few searches using some unique directory names like newmm, calldll, and shentou from the PDB paths, we can surface additional samples to examine further.
pe.pdb_filename.contains(r"newmm") && pe.pdb_filename.contains(r"calldll")
5a6a0e01949799dc72c030b4ad8149446624dcd9645ba3eefda981c3fda26472
57f64f170dfeaa1150493ed3f63ea6f1df3ca71ad1722e12ac0f77744fb1a829
fe4fad660bb44e108ab07d812f8b1bbf16852c1b881a5e721a9f811cae317f39
241737842eb17676b3603e2f076336b7bc6304accef3057401264affb963bef8
ee41eb21f439b1168ae815ca067ee91d84d6947397d71e214edc6868dbf4f272
2e3645c8441f2be4182869db5ae320da00c513e0cb643142c70a833f529f28aa
d176951b9ff3239b659ad57b729edb0845785e418852ecfeef1669f4c6fed61b
f65553c3e0f7aadf73a3f149cdba7345419edbc98f7ff6611c2368ca3859b353pe.pdb_filename.contains(r"newmm") && pe.pdb_filename.contains(r"shentou")
18f4f14857e9b7e3aa1f6f21f21396abd5f421342b7f4d00402a4aff5a538fa1
e0f109836a025d4531ea895cebecc9bdefb84a0cc747861986c4bc231e1d4213
d17fe5bc3042baf219e81cbbf991749dfcd8b6d73cf6506a8228e19910da3578
6fd7697efc137faf2d3ad5d63ffe4743db70f905a71dbed76207beeeb04732f2
3f0aa01ed70bc2ab29557521a65476ec2ff2c867315067cc8a5937d63bcbe815
As we discover additional samples, it’s useful to return to examine Variant Discovery on each to see if there are matches we haven’t yet uncovered via other means. For example, the SHA256: fe4fad660bb44e108ab07d812f8b1bbf16852c1b881a5e721a9f811cae317f39 that showed up searching for newmm and calldll in the PDB path has two variants. Both of these variants are signed and have similar PDB paths in them:
458df7daf3770068b3158c368a0c32f45fd6d14811317efceac74b15c6de19c1
Z:\完成\CallDll\x64\Release\lass.pdb
Signed: 上海笑聘网络科技有限公司
9d4e18ae979bdf6b57e685896b350b23c428d911eee14af133c3ee7d208f8a82
Z:\完成\CallDll\x64\Release\GoogleUpdate.pdb
Signed: 上海笑聘网络科技有限公司
According to Google Translate, 上海笑聘网络科技有限公司 is the Shanghai Xiaopin Network Technology Co., Ltd.
Pivoting on the common part of the PDB path we identify six additional samples:
pe.pdb_filename.contains(r"Z:\完成\CallDll\")
1e278cfe8098f3badedd5e497f36753d46d96d81edd1c5bee4fc7bc6380c26b3
8218c23361e9f1b25ee1a93796ef471ca8ca5ac672b7db69ad05f42eb90b0b8d
b4c470be7e434dac0b61919a6b0c5b10cf7a01a22c5403c4540afdb5f2c79fab
d31d135bc450eafa698e6b7fb5d11b4926948163af09122ca1c568284d8b33b3
357785be3a1f3437b08d29da264ad825115d948db03088e5826d1f0e15e21515
7b454f621055adc1fd6177aff34637657207d9a7d3b2182c26cb240846259cf3Infrastructure Pivots
Looking at some of the C2 infrastructure from the ESET report, we also found two Linux binaries that are associated with the IP 199.231.211[.]19:
a2c3073fa5587f8a70d7def7fd8355e1f6d20eb906c3cd4df8c744826cb81d91
98b5b4f96d4e1a9a6e170a4b2740ce1a1dfc411ada238e42a5954e66559a5541Using Variant Discovery on those gives us an additional sample, SHA256:bf830191215e0c8db207ea320d8e795990cf6b3e6698932e6e0c9c0588fc9eff with C2: security-microsoft[.]net
And pivoting with Variant Discovery from this new sample uncovers another that connects to the C2 of update.centos-yum[.]com which briefly pointed to the IP: 199.231.211[.]19 in March of 2023. SHA256: 15412d1a6b7f79fad45bcd32cf82f9d651d9ccca082f98a0cca3ad5335284e45.
Appendix
While intrusions by cyber-espionage groups against organizations in Africa and South America may go unreported, a recent community effort has recently started to help track and support victims of these attacks. The Undermonitored Regions Working Group (URWG) was recently started to help track these incidents in the future. The Stairwell research team shared our discovery and analysis among the working group to enhance collective defender knowledge in the region.



