Threat report: xz backdoor
A backdoored xz library included in Fedora 41 liblzma compromises SSH authentication (CVE-2024-3094).
Now that we’re beyond the jokes scattered around social media for April 1st and the dust has begun to settle around the latest supply chain compromise, we want to show you how Stairwell helped our customers with the xz library backdoor — and how we’ll continue to do so for the next similar threat, and the next one, and the one after that.
On March 29, 2024, a researcher discovered an intentional backdoor that had been placed into the xz library, which is used by OpenSSH through the lzma library. The backdoor targeted x86-64 builds of OpenSSH and allowed pre-authentication access to a compromised system. The compromised libraries were distributed in Fedora 41 but do not appear to have been included in other major distributions such as Redhat, Debian, or Ubuntu.
The Stairwell platform had detection for the xz backdoor initially via a YARA rule added by Silas Cutler as of Friday 2024-03-29T08:26Z. As Stairwell automatically collects, analyzes, and perpetually reanalyzes all interesting files in an environment, from this point forward, any Stairwell customer potentially affected by the backdoor knows exactly where and when this malicious code entered their environment. Equally important, if they were not affected, they have the evidence of absence — evidence that this threat is not in their environment — which they can provide to auditors, risk management, or their own management.
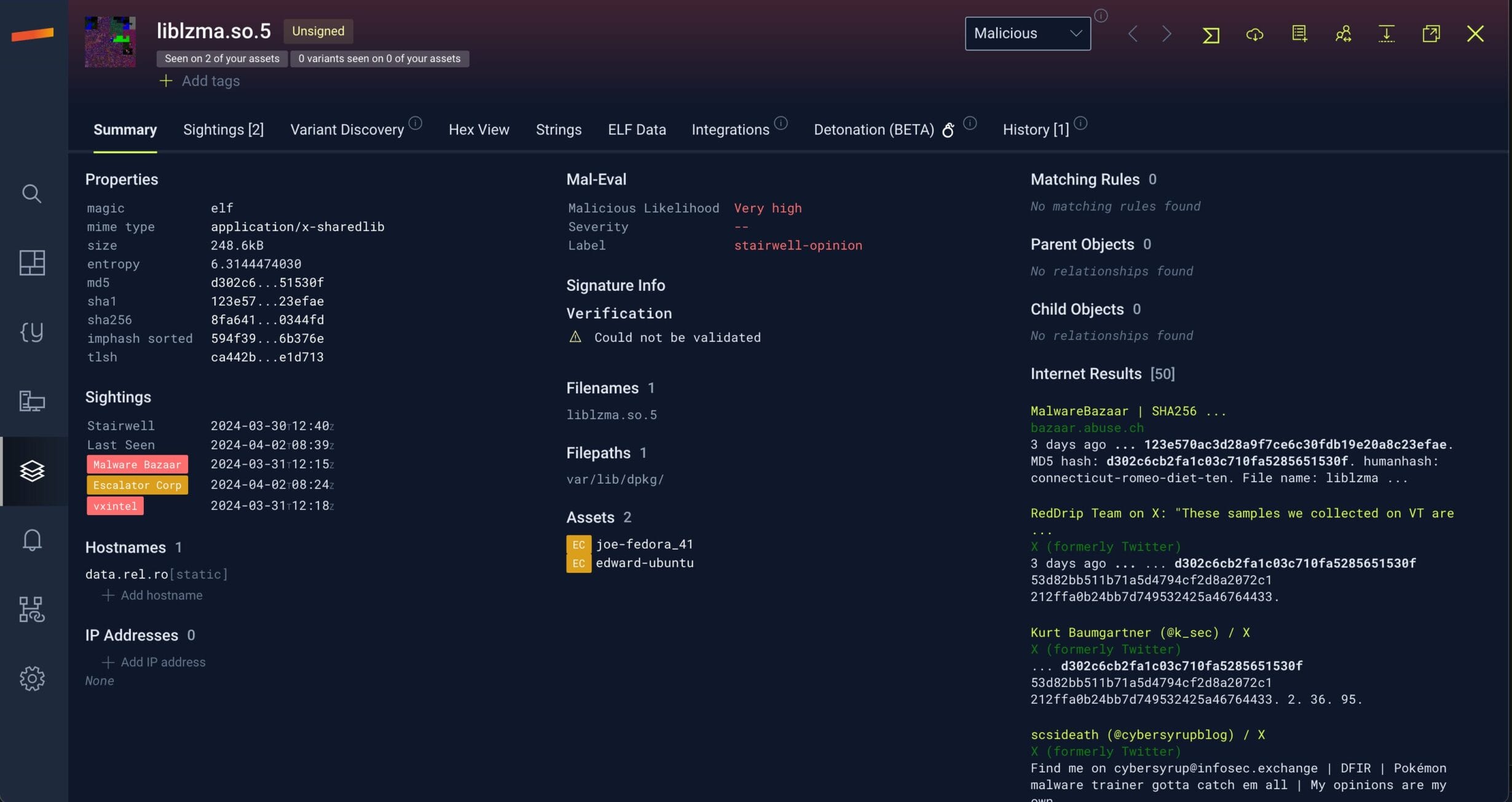
Image 1: A sample of a file with the backdoor uploaded to the Stairwell platform.
To enable our customers to automatically find and analyze indicators of compromise (IOCs) in their environment, the Stairwell team uploaded a Threat Report containing xz backdoor IOCs within the platform. This Threat Report will search across every single current and future file in your environment for the backdoor.
Unfortunately, as we all know too well, this is not a one-off scenario. Just as was seen with previous exploits and supply chain attacks like Log4j and 3CX, we are able to quickly keep your security team informed — helping to protect your organization now and into the future.
If you’re not a Stairwell user, detecting the backdoor manually remains an option via the xz_backdoor YARA rule or by identifying compromised liblzma binaries from the IOCs section below. However, with Stairwell, you’re not just reacting. The search and detection is fully automated and continuous, allowing you to stay ahead, fully informed, and more secure.
IOCs for xz backdoor
5d9f751a8311dab1c3fe3ec7ee8639cda5b451c305d58075f80e47ec8663e220
f19f29bbde3d6a6777fa7524179f68583a19278494019c289b6b9d59e5be9fd8
b0f95b124073faaac4415aefa4bb3985f287318efa8db702303f68dd650da349
aaaaf9a12d38dac328c74b45a2e6ea43950c85ecb010406d4092594cd904edc3
fcd4d1ba8a4def4e7178c27513a2897001019722f131efe7c4f6b940f231071b
c292bc94bb3a4d631ee458b22d633268e0a74733838f4b8638cd164bf150c9c5
f50ee33bab6abc93164577ca80f111d77595659842920d04a4d22e184f675d14
5448850cdc3a7ae41ff53b433c2adbd0ff492515012412ee63a40d2685db3049
b418bfd34aa246b2e7b5cb5d263a640e5d080810f767370c4d2c24662a274963
605861f833fc181c7cdcabd5577ddb8989bea332648a8f498b4eef89b8f85ad4
319feb5a9cddd81955d915b5632b4a5f8f9080281fb46e2f6d69d53f693c23ae
8fa641c454c3e0f76de73b7cc3446096b9c8b9d33d406d38b8ac76090b0344fd
cbeef92e67bf41ca9c015557d81f39adaba67ca9fb3574139754999030b83537
xz backdoor YARA rule
rule xz_backdoor
{
meta:
author= "Silas Cutler"
description = "Detection for backdoor in xz 5.6.1"
ref = "https://www.openwall.com/lists/oss-security/2024/03/29/4"
hash="cbeef92e67bf41ca9c015557d81f39adaba67ca9fb3574139754999030b83537"
version = "0.1"
strings:
$ = {f3 0f 1e fa 55 48 89 f5 4c 89 ce 53 89 fb 81 e7 00 00 00 80 48 83 ec 28 48 89 54 24 18 48 89 4c 24 10}
condition:
all of them
}



