ChamelGang and ChamelDoH: A DNS-over-HTTPS implant
The Stairwell Threat Research team has recently identified various tools used in intrusions by ChamelGang, a sophisticated threat actor with a nexus to China. ChamelGang has previously been observed targeting energy, aviation, and government organizations in Russia, the United States, Japan, Turkey, Taiwan, Vietnam, India, Afghanistan, Lithuania, and Nepal.
The original report, published by Positive Technologies, mainly focuses on the group’s Windows toolset. An overview of the tools recently identified by Stairwell’s Threat Research has revealed that this group has also devoted considerable time and effort to researching and developing an equally robust toolset for Linux intrusions. One such example is ChamelDoH, a C++ implant designed to communicate via DNS-over-HTTPS (DoH) tunneling.
This report is the first in a series detailing the capabilities and detection of various tools in ChamelGang’s intrusion arsenal.
Technical overview
The sample 34c19cedffe0ee86515331f93b130ede89f1773c3d3a2d0e9c7f7db8f6d9a0a7 is a large C++ binary designed for remote access to the system it is installed on and communicates with configured command-and-control (C2) infrastructure via DoH tunneling.
The sample utilizes a modified base64 alphabet to encode its communication as subdomains for a malicious, actor-controlled nameserver. The implant collects various portions of system information to profile the infected machine and is capable of basic remote access operations such as file upload, download, deletion, and execution.
Information gathering
Upon execution, the implant will utilize various system calls to generate a JSON object containing assorted pieces of reconnaissance data. The keys of the JSON and a description of each value have been included below.
Table 1: Information gathered by ChamelDoH upon execution
DNS-over-HTTPS tunneling
ChamelDoH is novel in its method of command-and-control (C2). The implant’s C2 configuration is a JSON object containing two keys. The keys of the JSON and a description of each value have been included below.
The sample 34c19cedffe0ee86515331f93b130ede89f1773c3d3a2d0e9c7f7db8f6d9a0a7 contains the following configuration (which has been defanged):
{
ns_record: [
"ns1.spezialsex[.]com",
"ns2.spezialsex[.]com"
],
doh: [
https://8.8.8.8/resolve?type=TXT&name=,
https://8.8.4.4/resolve?type=TXT&name=,
https://1.1.1.1/dns-query?type=TXT&name=,
https://cloudflare-dns.com/dns-query?type=TXT&name=,
https://dns.google.com/resolve?type=TXT&name=
]
}Figure 2: ChamelDoH configuration JSON
This configuration is then used by the implant to craft DoH requests using the configured providers and malicious nameservers, encoding its C2 communications as subdomains of the malicious nameserver and issuing TXT requests for the generated domain containing the encoded C2 communications.
Due to these DoH providers being commonly utilized DNS servers for legitimate traffic, they cannot easily be blocked enterprise-wide. Additionally, HTTPS prevents inspection of these requests without man-in-the-middling the traffic, so defenders cannot easily identify what domain requests are being made over DoH and selectively detect or prevent anomalous traffic such as ChamelDoH’s encoded communications. The result of this tactic is akin to C2 via domain fronting, where traffic is sent to a legitimate service hosted on a CDN, but redirected to a C2 server via the request’s Host header – both detection and prevention are difficult. A diagram has been included below to better illustrate its communications.
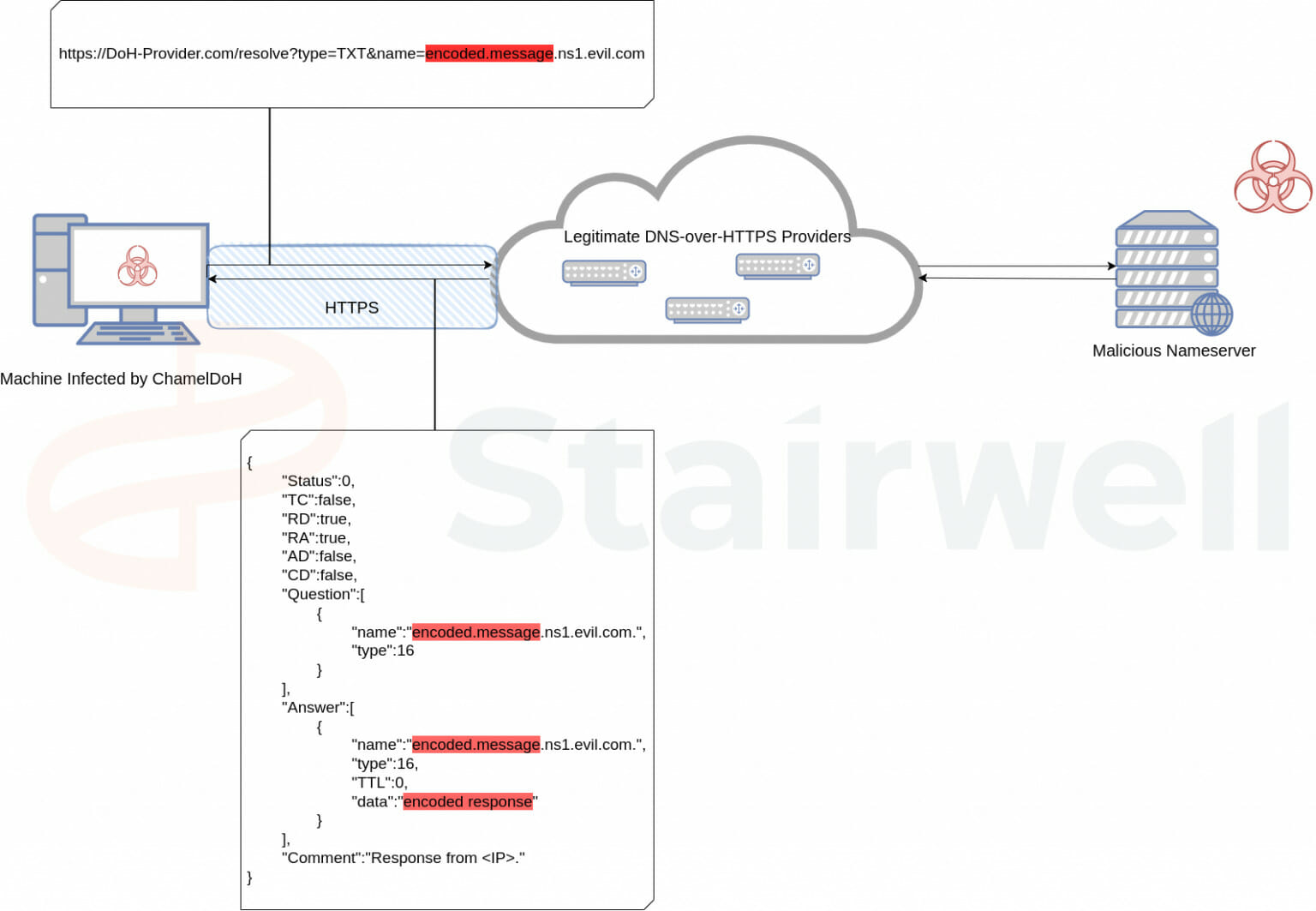
Figure 3: Example DNS-over-HTTPS tunneling diagram
ChamelDoH encrypts its communication using AES128 and base64 encodes the result so that it can be prepended as a subdomain. Since the base64 alphabet contains some non-alphanumeric characters, ChamelDoH utilizes a modified base64 alphabet to ensure the encoded data can be transmitted via DNS. It substitutes these characters with multi-character strings that have been detailed in the following table:
Table 3: ChamelDoH base64 alphabet substitutions
Since the DNS requests are TXT requests, the malicious C2 server is able to respond with arbitrary data within the response, and thus utilizes the standard base64 alphabet for its responses.
Capabilities
The implant is capable of basic remote access operations such as file upload, download, deletion, and execution. A list of all implemented commands has been included below.
Table 4: ChamelDoH commands
Variant analysis
Utilizing Stairwell’s next-generation variant discovery and analysis capabilities, the Stairwell Threat Research team identified a total of 10 samples of ChamelDoH. Notably, one sample is publicly available on third-party malware repositories:
The sample 92c9fd3f81da141460a8e9c65b544425f2553fa828636daeab8f3f4f23191c5b was first uploaded to VirusTotal in December of 2022. As of June 2023, it is undetected on the platform by any vendor or community contributor, save for an informational rule indicating that the binary utilizes DoH for DNS resolution.
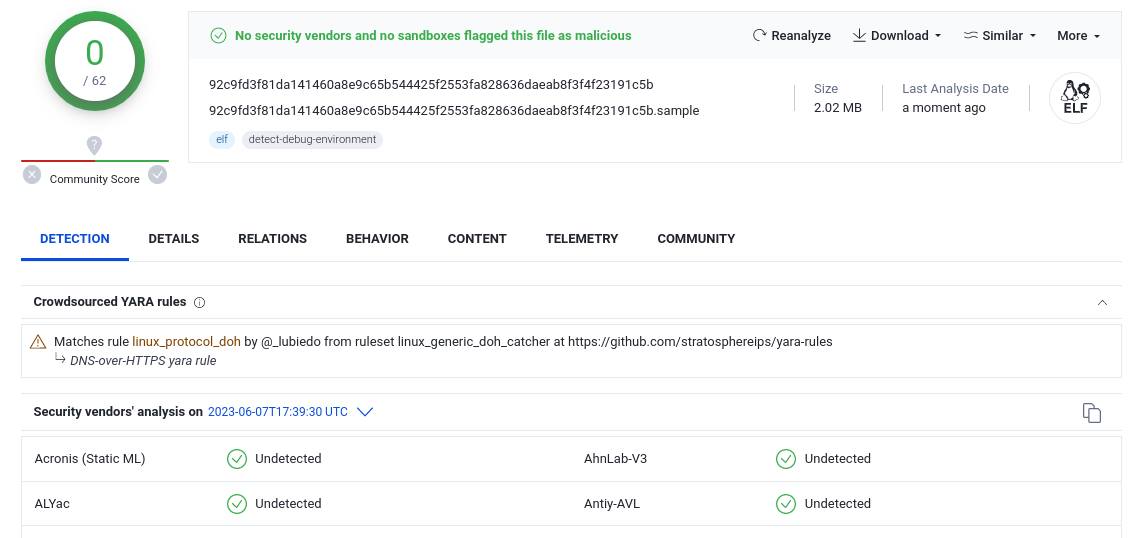
Figure 4: A sample of ChamelDoH undetected on VirusTotal as of 06/07/2023
A complete list of samples and their configured C2 servers has been included below.
Table 5: ChamelDoH variants and C2 servers
Attribution and further work
Stairwell Threat Research assesses that this malware family is highly likely to be developed by the same group detailed in previous reporting under the moniker ChamelGang. This assessment carries high confidence due to the presence of other intrusion tools that are uniquely attributable to ChamelGang that were identified in association with the deployment of samples of ChamelDoS:
- A configuration file for FRP configured to communicate with
45[.]91[.]24[.]3, which previously resolved to the domainupdate.microsoft-support[.]net. This domain and the subnet that the domain resolved to are both listed in Positive Technologies’ report on ChamelGang. - A sample of LinuxPrivilegeElevator, a small ELF binary that attempts to elevate to root privileges by calling
setuid(0),setgid(0),seteuid(0), andsetgid(0)before executing a given command. This tool is also detailed in Positive Technologies’ report.
Analysis of ChamelDoH and other previously unidentified tools utilized by ChamelGang is ongoing by the Stairwell Threat Research team. This report is the first in a series detailing the functionality of this actor’s toolset.
YARA
rule Stairwell_ChamelDoH_01
{
meta:
author = "Daniel Mayer ([email protected])"
copyright = "(c) 2023 Stairwell, Inc."
description = "Unique strings from a sample of ChamelDoH"
last_modified = "2023-06-07"
version = "0.1"
strings:
$ = "001020304050607080910111213141516171819202122232425262728293031"
$ = "resolve?type=TXT&name="
$ = "CONNECT_ONLY is required!"
$ = "[\"ns"
$ = "touch -r"
condition:
4 of them
}About Stairwell
The Stairwell platform helps organizations automate the detection and response efforts related to the threat outlined in this report and equips them with the tools needed to proactively monitor for future attacks.
By collecting every executable file in an organization’s environment, the Stairwell platform enables security teams to stay a step ahead with AI-based detection and analysis of malware and unknown variants present within your environment.
Conduct a full threat assessment in minutes, automatically and continuously uncover malware and its variants, and instill confidence that you’re better protected now, in the past, and in the future.