Exmatter: Clues to the future of data extortion
With contributions from Shelby Kaba, Director of Special Operations, Cyderes.
From the advent of big game hunting (BGH) to the proliferation of ransomware-as-a-service (RaaS) and data leak sites (DLS), the data extortion landscape is constantly experiencing new innovations from threat actors as well as acronyms from the security firms that track them. In this joint report, Cyderes and Stairwell explore hints of a new tactic found in the exfiltration tool used by an affiliate of BlackCat/ALPHV, discovered during an investigation by Cyderes.
During a recent Cyderes incident response, the team found and analyzed the tool in relation to a BlackCat/ALPHV ransomware investigation. Cyderes performed an initial assessment, discerning that the sample is an exfiltration tool with hardcoded sftp credentials. Following this, Cyderes leveraged the Stairwell platform for additional analysis.
The sample was also delivered to Stairwell’s Threat Research Team, where partially-implemented data destruction functionality was discovered upon analysis. The use of data destruction by affiliate-level actors in lieu of RaaS deployment would mark a large shift in the data extortion landscape and would signal the balkanization of financially-motivated intrusion actors currently working under the banners of RaaS affiliate programs.
Technical overview
The sample ad5002c8a4621efbd354d58a71427c157e4b2805cb86f434d724fc77068f1c40 is a .NET executable designed for data exfiltration using ftp, sftp, and webDAV protocols, and contains functionality for corrupting the files on disk that have been exfiltrated. The exfiltration behavior of this sample aligns closely with previous reports of Exmatter, a .NET exfiltration tool used by at least one affiliate of the BlackMatter ransomware group. The sample in question was observed by Cyderes in conjunction with the deployment of BlackCat/ALPHV ransomware, which is allegedly run by affiliates of numerous ransomware groups, including BlackMatter.
Directory traversal and exfiltration
In a routine named Sync, the malware iterates over the drives of the victim machine, generating a queue of files that match a hardcoded list of the following extensions, that are between 4096 bytes and 67108864 bytes (~67MB) in size:
Table 1: File extensions marked for exfiltration
All files matching the aforementioned file extensions are added to the queue for exfiltration, unless they are located within a directory specified in the malware’s hardcoded blocklist.
Table 2: Directory locations excluded from file exfiltration
The malware is capable of exfiltrating queued files by uploading them via sftp, ftp, or webDAV. This sample is configured to exfiltrate files over sftp with the username user2 and the password ytytrTRTYRTrfdfdf544535!!gfg to the actor-controlled IP address 128.199.145[.]18. The exfiltrated files are written to a folder with the same name as the victim machine’s hostname on the actor-controlled server.
Data destruction
There is a class defined within the sample named Eraser that is designed to execute concurrently with the routine Sync. As Sync uploads files to the actor-controlled server, it adds files that have been successfully copied to the remote server to a queue of files to be processed by Eraser. While the queue is not empty, two files from the queue are selected. A randomly sized chunk, starting at the beginning of the second file, is read into a buffer and then written into the beginning of the first file, overwriting it and corrupting the file (Figure 1). The act of using legitimate file data from the victim machine to corrupt other files may be a technique to avoid heuristic-based detection for ransomware and wipers, as copying file data from one file to another is much more plausibly benign functionality compared to sequentially overwriting files with random data or encrypting them.
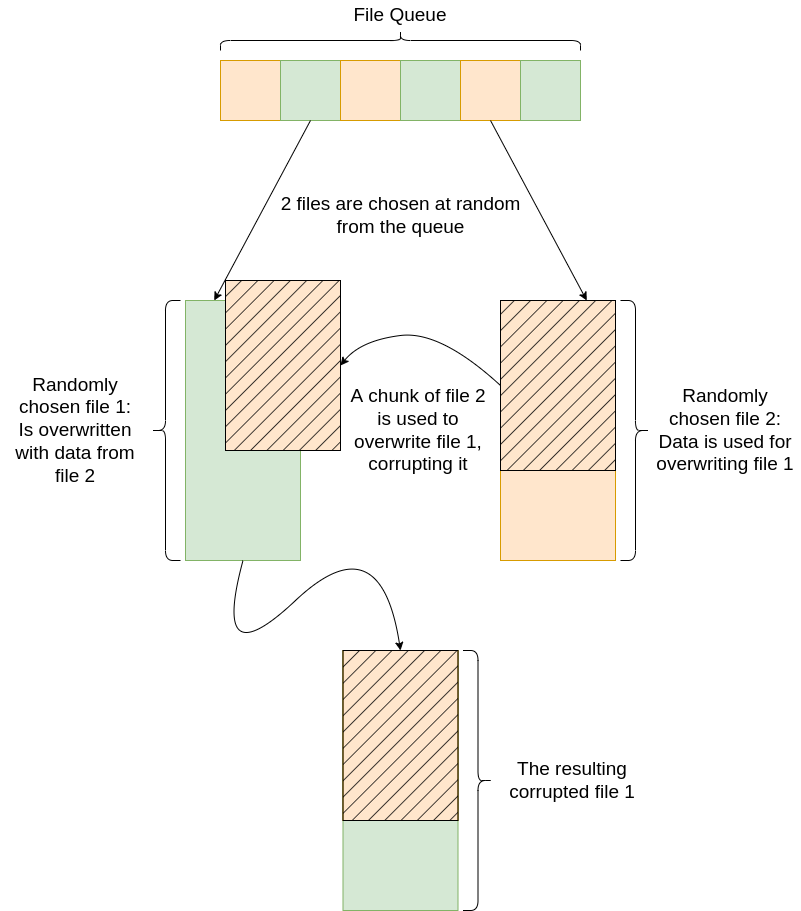
Figure 1: Exmatter file corruption diagram
The data destruction capabilities of Exmatter are seemingly still under development, as evidenced by multiple artifacts within the sample. Some of them are as follows:
- The second file’s chunk length, which is used to overwrite the first file, is randomly decided and could be as short as one byte long.
- There is no mechanism for removing files from the corruption queue, meaning that some files may be overwritten numerous times before the program terminates, while others may never have been selected.
- The function that instantiates the
Eraserclass, namedErase, does not appear to be fully implemented and does not decompile correctly.
Motivation
There are multiple potential reasons why a ransomware operator working under a Ransomware-as-a-Service (RaaS) affiliate program such as BlackCat/ALPHV would develop data destruction functionality within their exfiltration tool. With data exfiltration for DLS extortion now the norm, each affiliate is already exfiltrating all data deemed important from their victims, and in this sample’s case, keeping the exfiltrated data categorized by system.
With such a robust copy of the victim business’s data collected, encrypting the same files on disk becomes a redundant, development-heavy task compared to data destruction. Creating stable, robust ransomware is a far more development-intensive process than creating malware designed to corrupt the files instead, renting a large server to receive exfiltrated files and returning them upon payment.
Affiliates have also lost out on profits from successful intrusions due to exploitable flaws in the ransomware deployed, as was the case with BlackMatter, the ransomware associated with previous appearances of this .NET-based exfiltration tool. Cybersecurity firm Emsisoft was able to create a decryptor for BlackMatter, allowing victims to decrypt their environments without paying the threat actors. Data destruction ensures that the actor maintains the only copy of the victim’s files post-intrusion, eliminating any chance of data recovery without payment due to the bad luck of being an affiliate to a flawed RaaS, which may have been the case for the very affiliate developing this tool. Additionally, for each extorted payment received, the operator would retain 100% of the ransom payment, as opposed to paying a percentage to the RaaS developers.
These factors culminate in a justifiable case for affiliates leaving the RaaS model to strike it out on their own, replacing development-heavy ransomware with data destruction.
Assessments
Due to significant behavioral overlap with previous public reporting of heavily obfuscated versions of Exmatter, Stairwell assesses that the sample ad5002c8a4621efbd354d58a71427c157e4b2805cb86f434d724fc77068f1c40 is almost certainly an unobfuscated sample of the Exmatter exfiltration tool.
The development of capabilities to corrupt exfiltrated files within the victim environment marks a shift in data ransom and extortion tactics. With data exfiltration now the norm among threat actors, developing stable, secure, and fast ransomware that reliably encrypts files across various operating systems (OS), architectures, and OS versions is a redundant and costly endeavor compared to corrupting files and using the exfiltrated copies as the means of data recovery.
Artifacts within the sample indicate that the development of Exmatter is ongoing. Due to the nascent nature of the data destruction functionality within Exmatter, Stairwell assesses that data extortion actors are likely to continue experimenting with data exfiltration and destruction with increasing prevalence. This assessment carries moderate confidence due to its ease of implementation and the increasingly redundant nature of on-disk encryption with the ubiquity of data exfiltration as a part of modern extortion-motivated intrusions. The financial factors mentioned above also support the assessment that affiliate-level operators will experiment with data destruction as a RaaS replacement.
YARA
rule Stairwell_Exmatter_01 : ransomware dotnet
{
meta:
author = "Daniel Mayer ([email protected])"
copyright = "(c) 2022 Stairwell, Inc."
description = "Cleartext strings from an unobfuscated sample of Exmatter"
last_modified = "2022-08-23"
version = "0.1"
strings:
// Status strings
$ = "Commercial use only!" wide
$ = "We have {0} to upload and {1} completed" wide
$ = "Sending a report..." wide
// PowerShell used to end the process
$ = "-C \"Stop-Process -Id {0}; Start-Sleep 3; Set-Content -Path '{1}' -Value 0\"" wide
condition:
2 of them
}


