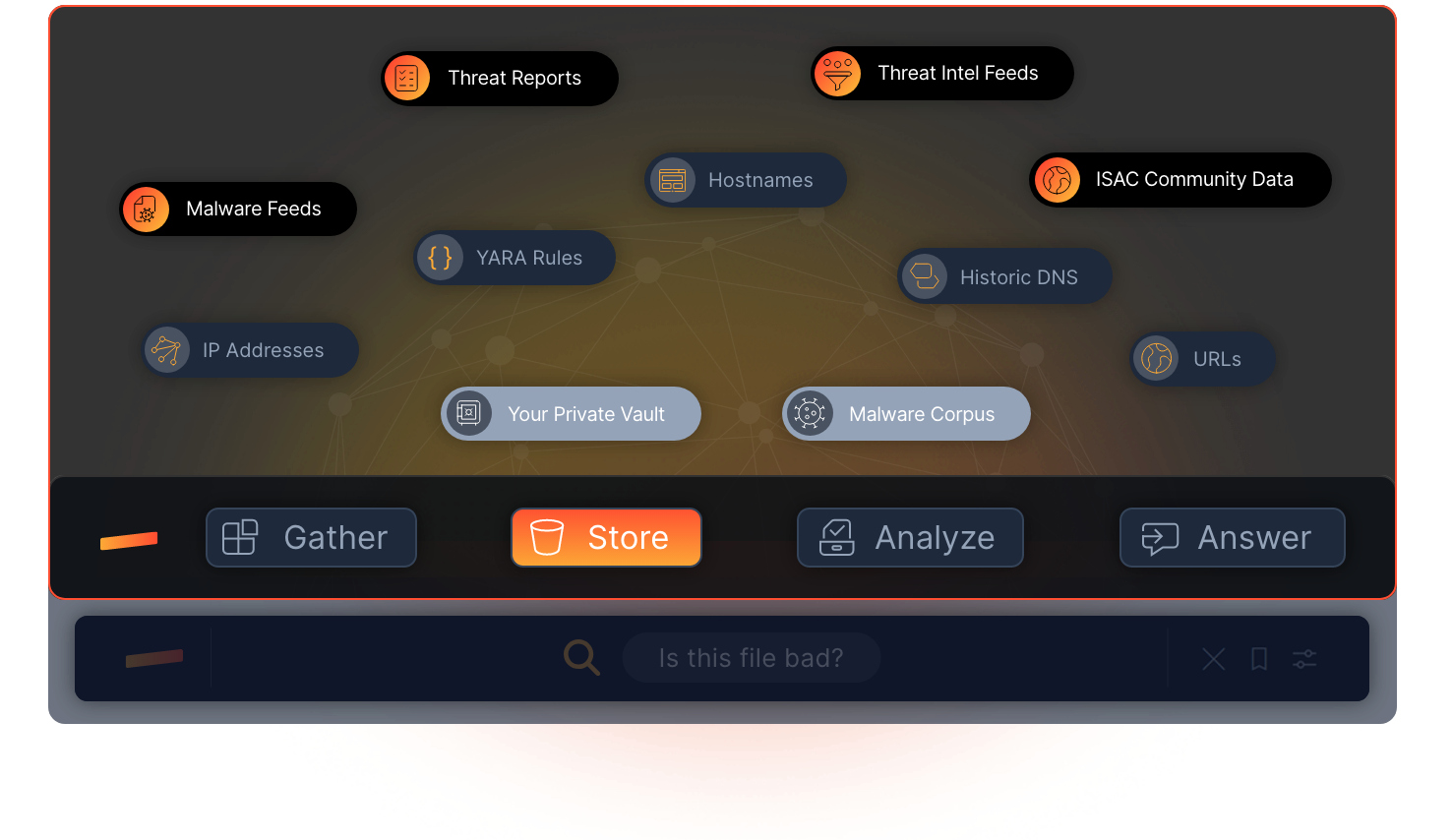
HOW IT WORKS
STORE EVERYTHING. PRIVATELY.
Enterprises don’t store the complete history of every file from every endpoint for one reason. It is brutally hard at scale, and the storage bill scares people into settling for logs. CISOs also know the log-only standard is collapsing under its own volume.
Stairwell solves the storage and search problem by treating security as data search, and your files as the ground truth. With no logs involved.

HOW IT WORKS
Stairwell stores files from every endpoint, then correlates threat intelligence, finds malware variants, to answers questions about your environment with confidence. Built at planet scale requiring no additional log storage costs or ingestion fees, Stairwell is a search engine for your private files and stores one of the world’s largest malware corpuses.
EVERYTHING IN ONE PLACE
Enterprise files, malware, DNS, EDR alerts, IOCs, YARA rules, intel feeds, stored in one data lake.
PRIVATE BY DESIGN
Stored in a private vault. Your threat intelligence stays yours, and nobody else’s.
INVISIBLE TO ADVERSARIES
Attackers reverse engineer endpoint tools, but cannot study a SaaS system they cannot access.
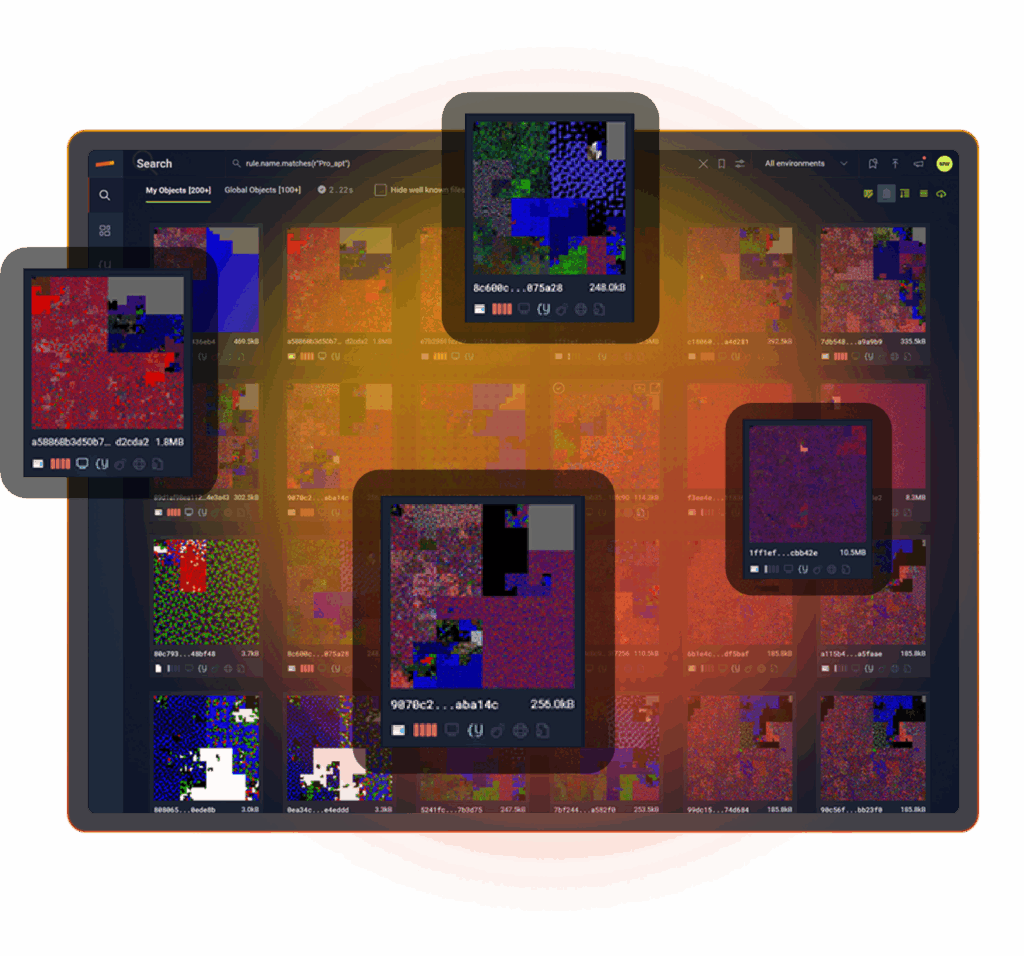
EVERY FILE STORED
Your most important dataset is your files. Stairwell stores every executable from every endpoint in your Private Vault and keeps it there, so you can answer security questions faster.
When a file changes, Stairwell stores the new version too and analyzes it again. No arbitrary retention windows. Once Stairwell is deployed, you build a complete file history for every device in your enterprise from that point forward.

FILE RETENTION. UNLIMITED
Keep every file, indefinitely, so you never lose the timeline. Stairwell shows exactly when changes happened and what changed.
As new IOCs emerge, Stairwell reruns them across your full history, letting you build a complete storyline for every file.

EXECUTABLES ONLY
You decide what gets uploaded to Stairwell. To protect privacy, Stairwell stores only executable files and scripts in its data lake.
More than 50 file types are supported, including EXE, DLL, MSI, CMD, ELF, PKG, PY, VB, and PS1.

MEMBERS-ONLY MALWARE SHARING
Stairwell includes a Members-only shared vault for trusted groups who share threat intelligence together. Members store malware samples and share IOCs, YARA rules, and reporting in one shared space, while every organization’s Private Vault stays separate.
This is how a community turns scattered intel into shared advantage. Stairwell was named Associate Vendor of the Year by RH-ISAC, and members use Stairwell to share threat intelligence in a members-only shared vault.

PRIVATE MALWARE CORPUS
Stairwell maintains a private malware corpus inside its data lake, growing by more than one million files every day. That depth gives you real hindsight, because today’s intel can recontextualize yesterday’s files.
Unlike public malware checking tools, Stairwell stays private and out of band. Adversaries cannot query it, study it, or learn what you know.
THREAT REPORT IOCS. INSTANTLY SEARCHABLE.
Stairwell stores a deep library of published threat reports in its data lake, including over 2,700 reports and more than 35,000 IOCs. That means your team can immediately check whether any reported indicators appear in your enterprise files, without manual parsing or copy paste searches.
You get faster answers, less busywork, and hours back every week.

ACTIVE DNS INTEL YOUR SOC TRUSTS
Stairwell continuously ingests over four billion active DNS requests every day and stores the responses as historical context for investigations. More data over time means a clearer story when you need to understand where a file connected and what it touched.
This goes beyond passive DNS. Stairwell tracks the shifting infrastructure adversaries use to deliver malware, so your SOC sees current reputation, not yesterday’s leftovers.

SHARED YARA AND PRIVATE RULES.
Stairwell includes a shared library of YARA rules available to every customer. Your own YARA rules remain private, and are only run against your enterprise files and Stairwell’s Malware Corpus.
With rules running continuously, you get daily visibility into any new files that match, without manual hunts.
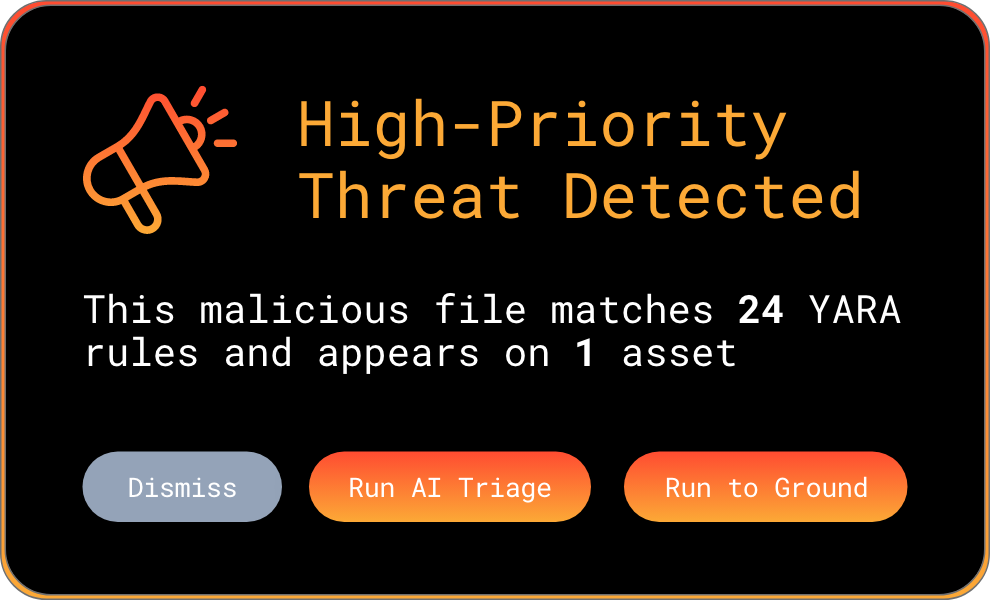
ENGINEERED FOR PLANET-SCALE
Built by Google and intelligence veterans. Web-scale indexing, YARA at ludicrous speed, and structured AI reasoning turn raw artifacts into instant understanding across everything you’ve ever seen.