VARIANT DISCOVERY
UNCOVER EVERY MALWARE VARIANT
Variant Discovery turns a single hash into visibility of the entire malware family. In seconds, understand all the infrastructure this malware family used across history. No YARA required.
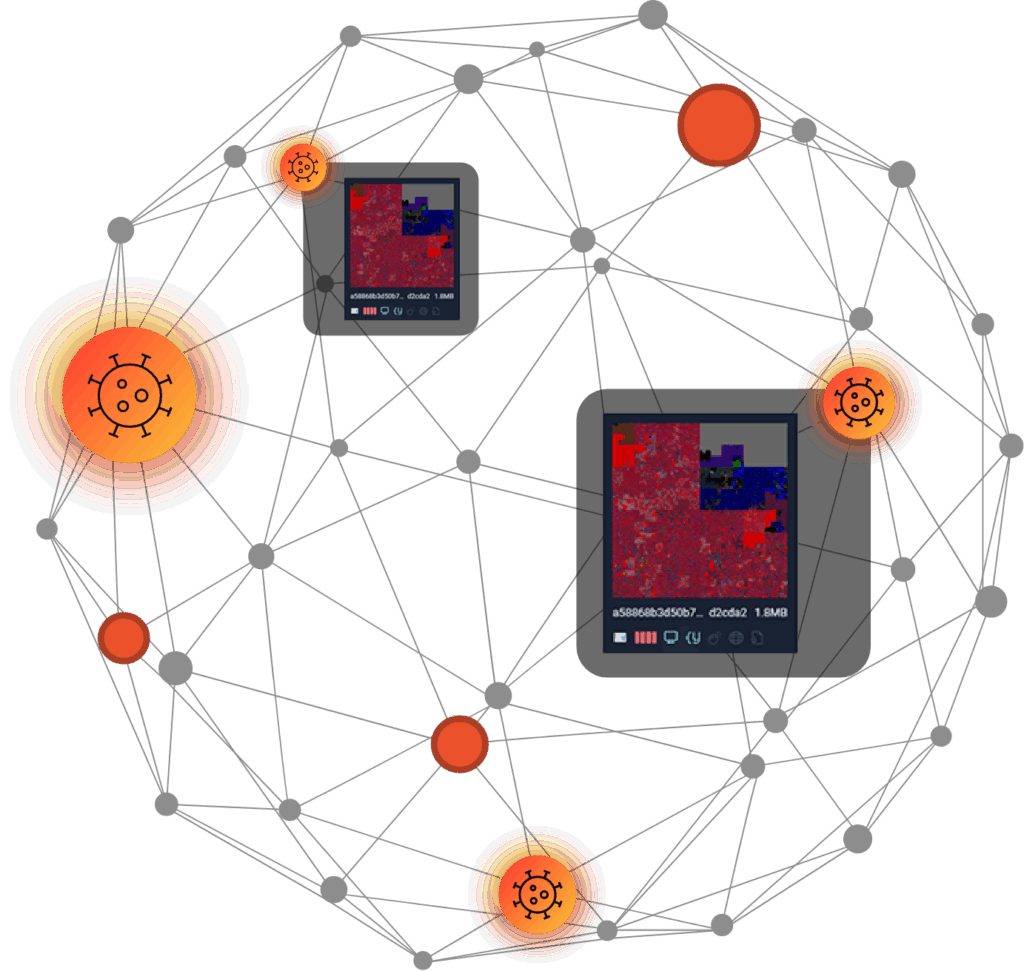
WHY VARIANT DISCOVERY MATTERS
EXPOSES EVASIVE VARIANTS
Analyzes file structure, behavior, and content to uncover the whole malware family.
REVEALS BLIND SPOTS
Reanalyzes your entire history turning yesterday’s blind spot into today’s insight.
MANUAL HUNTS DON'T SCALE
Turns one bad sample into a sweep for lookalikes, giving a campaign view beyond a single-file verdict.
“For hunting malware, Stairwell is the best way to do it.”
Michael Francess
Cybersecurity Advanced Threat and Response
| Wyndham Hotels & Resorts
WHAT IS VARIANT DISCOVERY?
Attackers don’t ship one binary. They ship dozens: repacked, re-signed, and slightly modified to evade detection. Variant Discovery finds the entire family from a single sample, so you stop playing whack-a-mole with hashes.
YOUR PRIVATE VAULT
Variant Discovery starts with Stairwell’s file-centric view of your environment. Every executable, script, and artifact is stored in your private, encrypted vault and not a public crowdsourced pool.
- Every file you’ve ever seen is searchable.
- Nothing ages out because a log pipeline rolled over.
- Your files, analyses, and verdicts are never exposed to adversaries giving you the advantage.

FINDS STRUCTURAL SIMILARITY
Attackers change what’s easy: packers, signatures, minor code tweaks. Hash-based detection dies instantly. Variant Discovery examines the underlying structure of files to identify lookalikes that share real DNA.
- Goes beyond hashes and looks at code structure, sections, imports, relationships
- Groups files that “feel” related even when their surface details differ.
- Surfaces clusters of variants tied to a single campaign or tooling set.
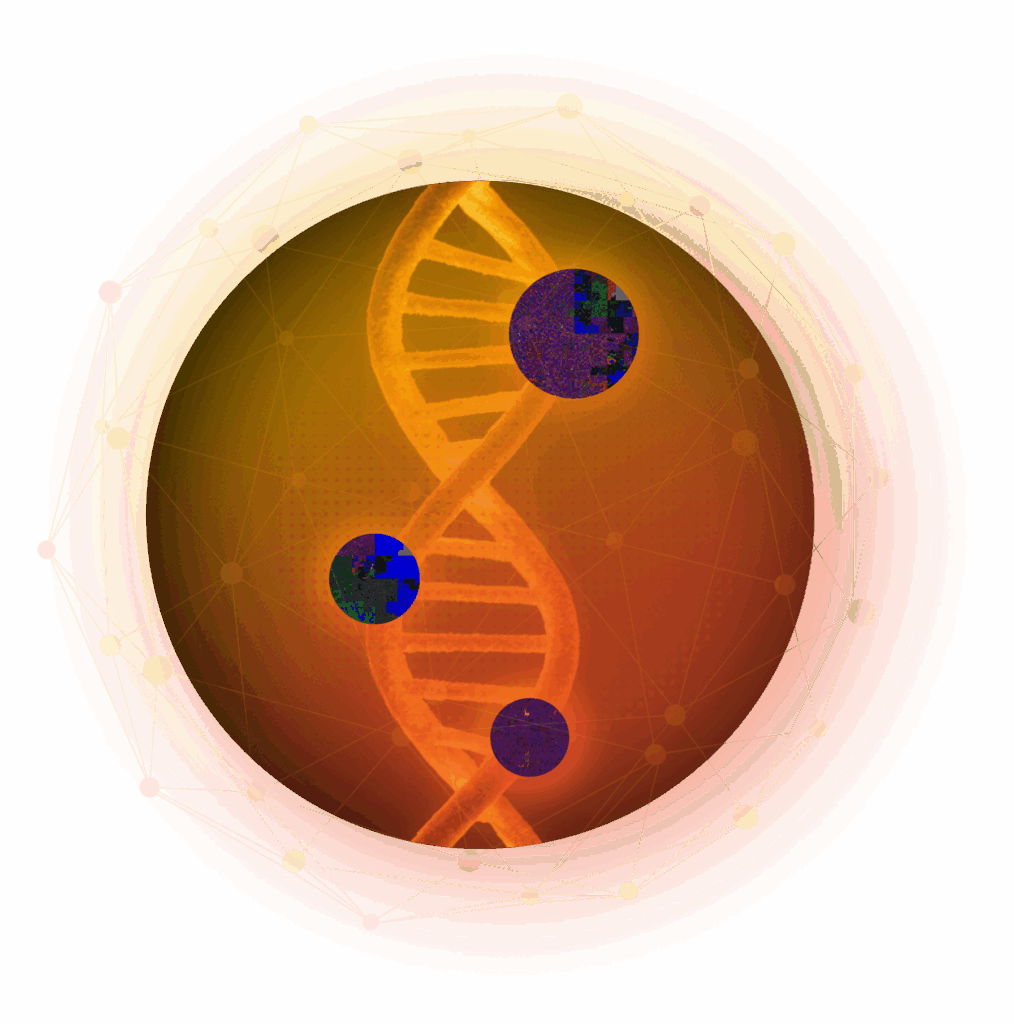
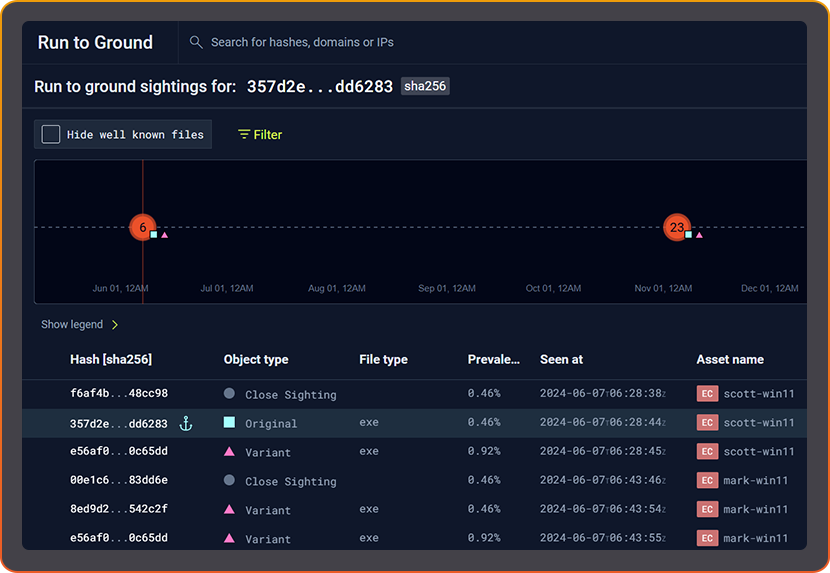
MAP THE ENTIRE MALWARE FAMILY
Catching a single sample is useful. Understanding the entire operation is better. Variant Discovery doesn’t stop at the file, it maps the malware family tree.
- See how variants evolved over time in your environment.
- Trace propagation: which hosts, which users, which time windows.
- Pivot from one IOC to the full spread of related artifacts and infrastructure.
In seconds, one hash becomes complete breach visibility.
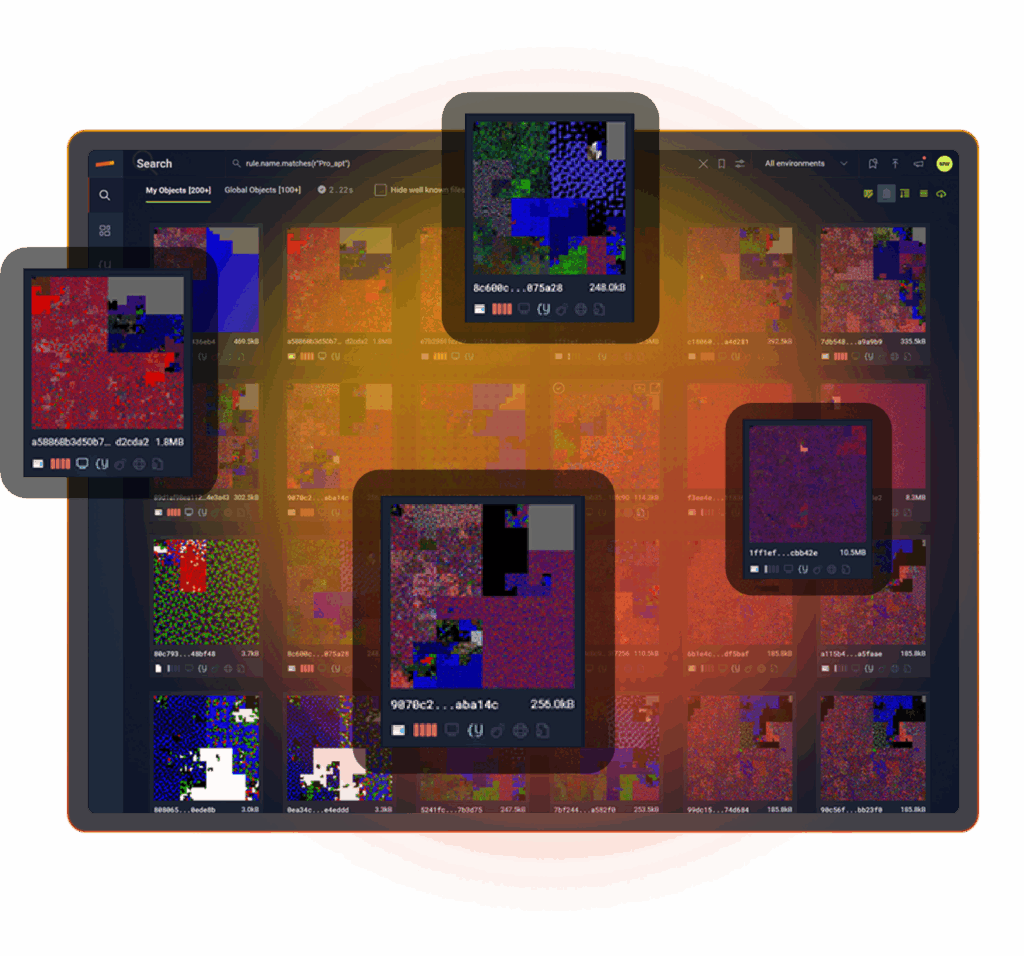
THREAT REPORTS MEETS VARIANT DISCOVERY
As new threat intel, YARA rules, and IOCs from threat reports arrive Stairwell’s Variant Discovery gains insight. At the click of a button Stairwell reanalyzes your entire file corpus in your private vault, lighting up variants that were invisible at first pass.
- New intel re-scores old files.
- Hidden variants from months ago suddenly become visible.
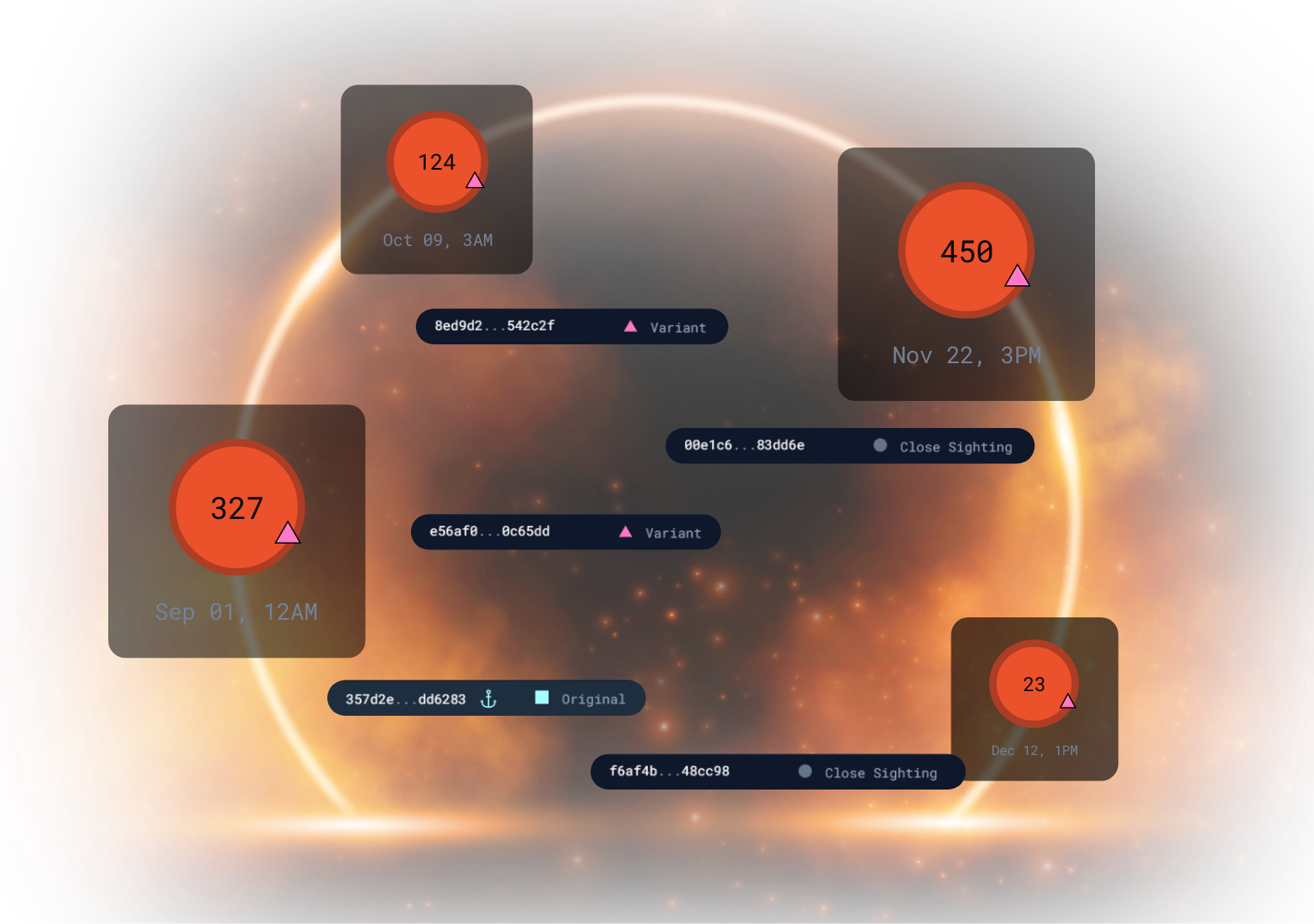
FROM ALERT TO “RUN TO GROUND”
Variant Discovery plugs into Stairwell’s broader investigation workflow. When an alert fires, Variant Discovery automatically asks: What else looks like this? And where it may have been?
- One click from sample to family, from IOC to campaign.
- Prove containment by showing where variants did, and didn’t, land.
- Replace “we think we got it” with hard evidence from your own files.
THE HIDDEN
MALWARE REPORT
Threat reports are a starting point. Stairwell goes further and finds the look-alikes. On average, we uncover 157% more variants, or 20+ additional malware variants per published threat report.

ENGINEERED FOR PLANET-SCALE
Built by Google and intelligence veterans. Web-scale indexing, YARA at ludicrous speed, and structured AI reasoning turn raw artifacts into instant understanding across everything you’ve ever seen.