Co-authored by Chris St. Myers and Silas Cutler
On January 2nd, 2024, Johann Aydinbas shared on Twitter what appeared to be a 3proxy sample (SHA256:eccfd9f2d1d935f03d9fbdb4605281c7a8c23b3791dc33ae8d3c75e0b8fbaec6) that had been signed with a Microsoft Windows Hardware Compatibility certificate and contained a C2 of catalog.micrisoftdrivers[.]com. Concerns about binaries signed by Microsoft Windows Hardware Compatibility certificates have come up in the past, as detailed in these blogs from SentinelOne and Mandiant.
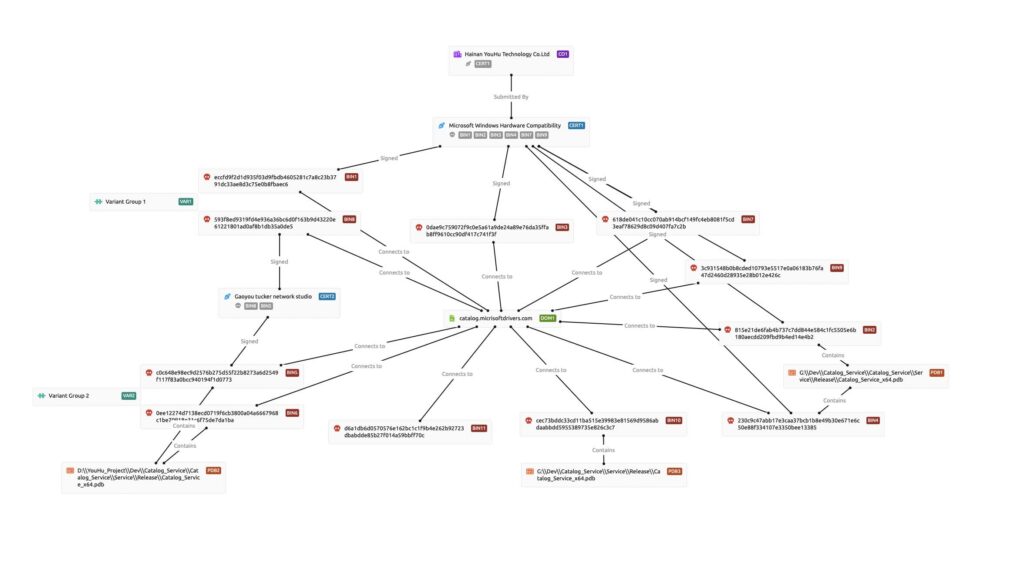
Further investigation by the Stairwell threat research team revealed that “Hainan YouHu Technology Co. Ltd” was responsible for submitting this file to Microsoft for signing. This company is known for developing an Android screen-sharing app named LaiXi (available at laixi[.]app). This app is designed for bulk management of mobile devices and content promotion on social media. Both the Windows and Android versions of this app are distributed via dl.cnhack[.]com. Notably, the malicious sample under scrutiny originated from a file named LaiXi_setup.exe.
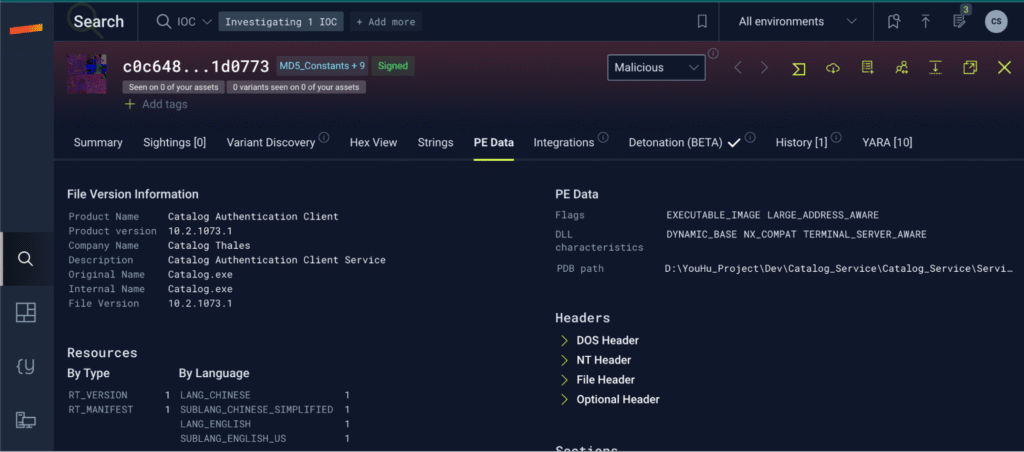
Image: Using Stairwell’s Variant Discovery to identify potential malicious variants of the original file.
Our initial steps involved using Stairwell’s Variant Discovery tool to search across our 700M+ file corpus for similar files. This led us to identify a closely related sample with a 99% match, bearing the SHA256 hash: 593f8ed9319fd4e936a36bc6d0f163b9d43220e61221801ad0af8b1db35a0de5. This variant of malware was signed with a certificate from “Gaoyou tucker network studio.” Next, we wrote and deployed a couple of YARA rules to hunt for samples signed with these certificates.
Hunting across our samples with YARA on that certificate identifies a new hash, SHA256:c0c648e98ec9d2576b275d55f22b8273a6d2549f117f83a0bcc940194f1d0773, which also connects to the previously documented C2. Additionally, this sample has a PDB path with unique elements we can utilize for further pivots: D:\YouHu_Project\Dev\Catalog_Service\Catalog_Service\Service\Release\Catalog_Service_x64.pdb.
Summary
The use of certificates, particularly for code signing, presents significant security risks. Originally designed to assure users of software authenticity and integrity, certificates can create a false sense of security. Malicious actors often acquire certificates illicitly, even from underground markets, using them to give malware an appearance of legitimacy. This issue is compounded by weaknesses in certificate validation processes, where lax or circumvented issuing procedures diminish trust in certificate-based security.


Images: Example of certifications for sale on the internet.
A major concern is detecting malware signed with legitimate certificates. Security systems that automatically trust signed files can inadvertently allow malicious software to bypass detection. Furthermore, the trust in certificates is transitive: software signed by a trusted source is considered safe. This can be exploited if attackers manage to get their malware signed by a trusted certificate, leveraging this trust for malicious purposes.
While code-signing certificates are vital for cybersecurity, their misuse, validation challenges, and trust complexities highlight the need for a more comprehensive security approach. Relying solely on certificates is insufficient; a multifaceted security strategy and constant vigilance are essential, even for signed software.
This mystery around the purpose of this malware remains unsolved and the Stairwell Threat Research team is sharing this information in the hope that others with different visibility can contribute to unraveling the story.
Indicators of compromise (IoCs)
- SHA256:
eccfd9f2d1d935f03d9fbdb4605281c7a8c23b3791dc33ae8d3c75e0b8fbaec6- C2:
catalog.micrisoftdrivers[.]com - Compiled:
Sun Oct 8 17:05:40 2023 UTC
- C2:
- SHA256:
815e21de6fab4b737c7dd844e584c1fc5505e6b180aecdd209fbd9b4ed14e4b2- PDB:
G:\Dev\Catalog_Service\Catalog_Service\Service\Release\Catalog_Service_x64.pdb - C2:
catalog.micrisoftdrivers[.]com - Compiled:
Wed Jan 11 09:46:14 2023 UTC
- PDB:
- SHA256:
230c9c47abb17e3caa37bcb1b8e49b30e671e6c50e88f334107e3350bee13385- PDB:
G:\Dev\Catalog_Service\Catalog_Service\Service\Release\Catalog_Service_x64.pdb - C2:
catalog.micrisoftdrivers[.]com - Compiled:
Sun Mar 19 14:19:29 2023 UTC
- PDB:
- SHA256:
c0c648e98ec9d2576b275d55f22b8273a6d2549f117f83a0bcc940194f1d0773- PDB:
D:\YouHu_Project\Dev\Catalog_Service\Catalog_Service\Service\Release\Catalog_Service_x64.pdb - C2:
catalog.micrisoftdrivers[.]com - Compiled:
Sun Oct 8 17:05:45 2023 UTC
- PDB:
- SHA256:
0ee12274d7138ecd0719f6cb3800a04a6667968c1be70918e31c6f75de7da1ba- PDB:
D:\YouHu_Project\Dev\Catalog_Service\Catalog_Service\Service\Release\Catalog_Service_x64.pdb - C2:
catalog.micrisoftdrivers[.]com - Compiled:
Sun Oct 8 17:05:45 2023 UTC
- PDB:
- SHA256:
618de041c10cc070ab914bcf149fc4eb8081f5cd3eaf78629d8c09d407fa7c2b- C2:
catalog.micrisoftdrivers[.]com - Compiled:
Sun Mar 19 14:19:34 2023 UTC
- C2:
- SHA256:
593f8ed9319fd4e936a36bc6d0f163b9d43220e61221801ad0af8b1db35a0de5- C2:
catalog.micrisoftdrivers[.]com - Compiled:
Sun Oct 8 17:05:40 2023 UTC
- C2:
- SHA256:
3c931548b0b8cded10793e5517e0a06183b76fa47d2460d28935e28b012e426c- C2:
catalog.micrisoftdrivers[.]com - Compiled:
Sun Mar 19 14:19:29 2023 UTC
- C2:
- SHA256:
0dae9c759072f9c0e5a61a9de24a89e76da35ffab8ff9610cc90df417c741f3f- C2:
catalog.micrisoftdrivers[.]com
- C2:
- SHA256:
cec73bddc33cd11ba515e39983e81569d9586abdaabbdd5955389735e826c3c7- PDB:
G:\Dev\Catalog_Service\Service\Release\Catalog_Service_x64.pdb - C2:
catalog.micrisoftdrivers[.]com - Compiled:
Thu Jan 5 19:58:50 2023 UTC
(May be an earlier version – C2 was not encoded)
- PDB:
- SHA256:
d6a1db6d0570576e162bc1c1f9b4e262b92723dbabdde85b27f014a59bbff70c- C2:
catalog.micrisoftdrivers[.]com
- C2:
